Blog
Leading IT Cybersecurity Adaption
James V. Tarlton
7/20/2025
Abstract
This literature review examines the critical role of human factors in cybersecurity leadership discussed by William J. Triplet (2022), revealing that humans constitute a weakness in organizational security with research indicating that over 86% of cyber incidents involve human error or misconduct. The analysis of current literature demonstrates that cybersecurity leaders face significant challenges in addressing unintentional human behaviors, communication gaps, and organizational cultural deficiencies that contribute to security vulnerabilities. Key findings indicate that traditional technology-centric approaches are insufficient, and organizations require transformational leadership approaches that prioritize human-centered security strategies, comprehensive training programs, and cultural transformation initiatives. Recommendations include implementing behavioral security models, establishing cross-functional insider threat teams, developing continuous security awareness programs, and creating cybersecurity culture maturity frameworks that position employees as active defenders rather than passive compliance actors.
Problem Statement
Triplett (2022) stresses that while organizations invest billions in technological solutions, human factors remain the primary source of security vulnerabilities and breaches. Additional research reveals multiple interconnected issues stemming from inadequate attention to human elements in cybersecurity strategy. First, there exists a persistent knowledge gap where leaders treat cybersecurity as purely a technological challenge rather than a sociotechnical problem requiring human behavior management (McEvoy & Kowalski, 2019). This narrow-mindedness results in cybersecurity leaders who possess strong technical competencies but lack the interpersonal, communication, and cultural transformation skills necessary to effectively engage with non-technical employees (Cole, 2022).
Second, organizational cultures often exhibit security immaturity. Prakash & Pearlson suggest that employees demonstrate complacent attitudes toward cybersecurity responsibilities when leaders fail to establish accountability structures (2024). The literature indicates that organizations operate at basic cybersecurity culture maturity levels where employees believe "technology teams will keep us safe" (p. 3) rather than embracing personal responsibility for security, Prakash & Pearlson add. Third, traditional security awareness training approaches demonstrate limited effectiveness, with studies showing no significant correlation between recent annual training completion and employee ability to avoid phishing attacks (UC, Dept. of Computer Science, 2025). Finally, insider threats represent a growing challenge that requires sophisticated human factors analysis and behavioral intervention strategies (Watts, 2024) (Sifma, 2024).
Problem Statement
The systematic literature review conducted by Triplett (2022) provides comprehensive evidence that unintentional human factors significantly impact cybersecurity effectiveness across organizations. Analysis of 15 studies revealed consistent patterns of human vulnerabilities including employees forgetting to log out of systems, creating weak passwords, and unknowingly clicking malicious links due to limited cybersecurity knowledge. These behaviors stem from deeper organizational factors including inadequate leadership attention to human behavior, insufficient communication between technical and non-technical staff, and workplace stress that contributes to security fatigue (Pollini, et al., 2022).
McEvoy & Kowalski (2019) agree with Triplett’s assessment, stating that the sociotechnical systems perspective reveals that cybersecurity risks emerge from complex interactions between individual, organizational, and technological factors. They also suggest that current risk analysis methodologies focus primarily on technical and procedural requirements while systematically excluding sociotechnical considerations. This leaves organizations vulnerable to predictable human-centered attacks. The Behavioral Security Model demonstrates that sustainable security requires addressing four interconnected dimensions: knowledge, context, motivation, and behavior (SOSafe, 2025). Organizations that fail to address these dimensions comprehensively experience persistent security vulnerabilities despite substantial technological investments.
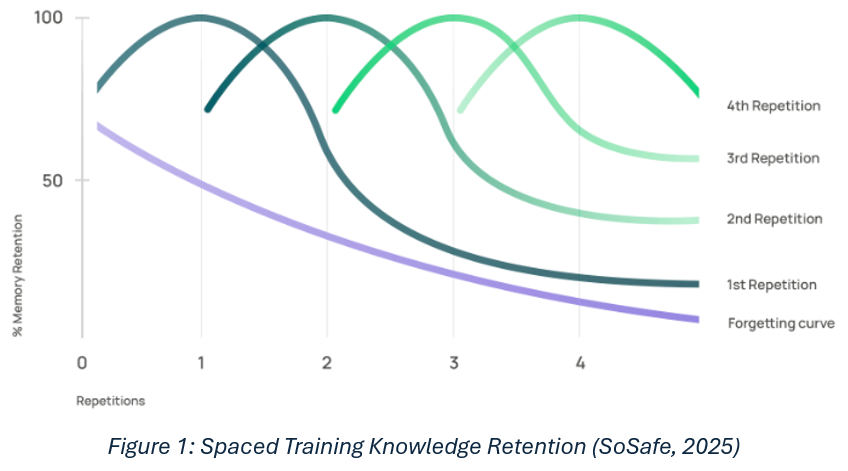
Per SoSafe, leadership competency analysis reveals significant gaps in cybersecurity leaders' ability to bridge technical and business domains while effectively communicating with diverse stakeholder groups. Moreso, SoSafe suggests managers facilitating repetitive training increases user memory retention (Figure 1). Research indicates that effective cybersecurity leaders require not only technical expertise but also business acumen, emotional intelligence, and transformational leadership capabilities (Corll, 2024) (Burton, et al., 2023). However, cybersecurity professionals are underrepresented in organizational leadership hierarchies and lack the social capital necessary to influence organizational behavior change. However, IT representation is trending upward (Llorca, 2024). Gartner suggests that 84% of the highest performing companies now include Chief Information Officers (CIOs) within their executive leadership teams (2025).
Nonetheless, the insider threat dimension presents particularly complex challenges requiring integration of human resources, legal, risk management, and cybersecurity functions. Watts (2024) suggests that organizations must distinguish between intentional and unintentional insider threats while implementing monitoring and intervention strategies that respect employee privacy and maintain organizational trust.
Alternative Solutions
Training and Awareness Enhancement Approaches
Research demonstrates that well-designed security awareness training can reduce phishing susceptibility from 60% to 10% within 12 months, with studies showing 80% of organizations reporting reduced staff susceptibility to phishing attacks (Daly, 2025). Continuous, behavior-focused training programs that incorporate psychological principles show promise for creating lasting behavioral change. Traditional annual training approaches show limited effectiveness, with recent studies finding no correlation between training recency and phishing resistance (UC, Dept. of Computer Science, 2025). Many training programs focus on knowledge transfer rather than behavior modification, resulting in awareness without corresponding behavioral change (HoxHunt, 2025).
Cybersecurity Culture Transformation Initiatives
Prakash & Pearlson’s (2024) culture maturity model provides structured framework for organizations to progress from basic security awareness to dynamic cybersecurity cultures where employees proactively identify and address threats. Everard (2025) suggests that cultural approaches address root causes of security vulnerabilities by aligning organizational values, attitudes, and beliefs with security objectives. However, Triplet (2022) stresses that culture transformation requires significant time investment and sustained leadership commitment, with outcomes difficult to measure quantitatively. Therefore, he suggests that cultural initiatives may face resistance from employees who view security requirements as burdensome rather than value-adding.
Technology-Enhanced Human Factors Management
Artificial intelligence and machine learning applications can identify behavioral anomalies and provide predictive insights for insider threat management, per Sifma (2024). Sifma also suggests that identity and access management systems can reduce human error by automating security controls and limiting exposure to mistakes. However, technology cannot address underlying behavioral human factors. Triplet (2022) and McEvoy & Kowalski (2019) suggest that over-reliance on technological solutions perpetuates the fundamental problem of treating cybersecurity as a technical rather than sociotechnical issues.
Leadership Development and Communication Enhancement
Developing cybersecurity leaders with strong communication and social skills enables better engagement with non-technical employees and executives (Corll, 2024). Leadership development programs can address the gap between technical expertise and business competencies (Triplet, 2022). However, it requires sustained investment and may not address systemic organizational issues contributing to security vulnerabilities. Leadership improvements may be insufficient without corresponding structural changes, per Triplet.
Recommendations / Reflection
Based on Triplet’s literature (2022), organizations should adopt an integrated Human-Centered Cybersecurity Leadership Framework that addresses technical and human dimensions of security. The priority is to implement a Behavioral Security Model which can address knowledge, motivation, and behavior with continuous learning programs that incorporate proven frameworks. Real-time feedback, social reinforcement, and practical exercises can help embed secure behaviors into daily routines.
A second recommendation is to establish cross-functional insider threat teams that bring together human resources, legal, privacy, risk management, and cybersecurity professionals. These professionals should address insider threats with an approach that stresses deterrence through a positive climate rather than relying solely on punitive measures. With transparency and trust, employees are encouraged to proactively report findings.
Third, leadership development must be prioritized to create transformational cybersecurity leaders. Effective leaders in this space require a blend of technical expertise, business acumen, and strong interpersonal skills. Leadership programs should emphasize emotional intelligence, adaptive communication, and motivation. Leaders who can bridge technical and non-technical gaps are better equipped to drive cultural change (Prakash & Pearlson, 2024).
Finally, organizations should invest in cybersecurity culture maturity assessment and development programs. These programs provide frameworks for enhancing the organization’s security culture, guiding the transition from basic compliance mindsets to dynamic, resilient cultures where all employees see themselves as active defenders (Everard, 2025). Technology alone is insufficient for sustainable security. True resilience requires a holistic approach that integrates behavioral science, cultural evolution, and leadership development. Organizations that commit to this comprehensive strategy will be better positioned to address evolving cyber threats, maintain operational effectiveness, and empower employees as essential partners in defense.
Bibliography
Burton, S. L., Burrell, D. N., Nobles, C., Jones, L. A., Illinois Institute of Technology, Capitol Technology University , & Embry-Riddle Aeronautical University. (2023). Exploring the Nexus of Cybersecurity Leadership, Human Factors, Emotional Intelligence, Inno Emotional Intelligence, Innovative Work Beha ork Behavior, and Critical , and Critical Leadership Traits. Scientific Bulletin, 28.
Cole, E. (2022, 2 10). How to be an Effective CISO by Being an Affective Communicator. Retrieved from secure-anchor.com/cybercrisis/: https://www.youtube.com/watch?v=jU2cQAxRodk&t=4s
Corll, B. (2024, 8 1). 5 behaviors for transforming your cybersecurity leadership. Retrieved from zscaler.com: https://www.zscaler.com/cxorevolutionaries/insights/5-behaviors-transforming-your-cybersecurity-leadership
Daly, J. (2025). How effective is security awareness training? Retrieved from usecure.io: https://blog.usecure.io/does-security-awareness-training-work
Everard, T. (2025). What is Cyber Security Culture and why does it matter for your organisation? Retrieved from paconsulting.com: https://www.paconsulting.com/insights/what-is-cyber-security-culture-and-why-does-it-matter-for-your-organisation
Gartner. (2025, 2 12). Gartner Executive FastStart for CIOs. Retrieved from gartner.com: https://www.gartner.com/en/chief-information-officer/insights/executive-faststart-cio
HoxHunt. (2025). How to Create Behavior Change With Security Awareness Training. Retrieved from hoxhunt.com: https://hoxhunt.com/lp/how-to-create-behavior-change-with-security-awareness-training
Llorca, M. (2024, 10 24). Today's CIO, Tomorrow's CEO: The Changing Landscape Of Corporate Leadership. Retrieved from forbes.com/councils/forbestechcouncil: https://www.forbes.com/councils/forbestechcouncil/2024/10/24/todays-cio-tomorrows-ceo-the-changing-landscape-of-corporate-leadership/
McEvoy, R., & Kowalski, S. (2019). Cassandra’s Calling Card: Socio-technical Risk Analysis and Management in Cyber Security Systems. CEUR Workshop Proceedings. vol. 2398. Retrieved from CEUR-WS.org/Vol-2398/Paper8.pdf
Pollini, A., Callari, T. C., Tedeschi, A., Ruscio, D., Save, L., Chiarugi, F., & Guerri, D. (2022). Leveraging human factors in cybersecurity: an integrated methodological approach. Cogn Technol Work, 371-390.
Prakash, M., & Pearlson, D. K. (2024). Cybersecurity Culture Maturity Model. Cybersecurity at MIT Sloan, MIT, CAMS24.1109.
Sifma. (2024, 7 1). Insider Threat Best Practices Guide, 3rd Ed. Retrieved from sifma.org: https://www.sifma.org/wp-content/uploads/2025/03/2024-SIFMA-Insider-Threat-Best-Practices-Guide-FINAL.pdf
SOSafe. (2025, 1 10). The Behavioral Security Model: A proactive approach to the human component of cyber security. Retrieved from sosafe-awareness.com: https://sosafe-awareness.com/en-us/blog/how-to-create-a-security-culture-the-behavioral-security-model/
Triplet, W. J. (2022). Addressing Human Factors in Cybersecurity Leadership. J. Cybersecur. Priv., 573–586.
UC, Dept. of Computer Science. (2025, 3 24). New Study Reveals Gaps in Common Types of Cybersecurity Training. Retrieved from cs.uchicago.edu: https://cs.uchicago.edu/news/new-study-reveals-gaps-in-common-types-of-cybersecurity-training/
Watts, L. (2024, 6 24). Unintentional Insider Threats: The Overlooked Risk. Retrieved from teramind.co/blog: https://www.teramind.co/blog/unintentional-insider-threat/
Beyond Voluntary IoT Standards
James V. Tarlton
6/11/2025
Abstract
The article "Cybersecurity Carrots and Sticks" by Hiller et al. (2024) address the persistent and worsening trend of cyberattacks, highlighting the limitations of current regulatory and voluntary approaches. The authors propose an incentive-based tax policy framework to spur stronger cybersecurity postures across the private sector. It involves combining tax credits (carrots) and penalties (sticks). This case analysis firstly evaluates the eƯectiveness of such an approach, drawing on Bruce Schneier’s examples and policy considerations to contextualize the urgency and complexity of the cybersecurity landscape. Schneier’s Click Here to Kill Everybody (2018) assesses risks emerging from the emergence of Internet of Things (IoT) devices. He systematically explores the causes of these security gaps and proposes a mix of policy, regulatory, and technical solutions. Secondly, this case analysis recommends prioritizing regulatory reform and realigning industry incentives. Which may help address the root causes of IoT insecurity. While Hiller et al.’s recommendations are robust and pragmatic, further global coordination and enforcement mechanisms are needed to fully meet the scale of the challenges outlined by Schneier.
Problem Statement
The central problem identified by Hiller et al. (2024) is the unsustainable spiral of cyberinsecurity in the United States, driven by a fragmented regulatory landscape, overreliance on self-regulation, and chronic underinvestment in cybersecurity, particularly among small and medium-sized enterprises. As Schneier (2018) illustrates, the rapid proliferation of IoT devices and the interconnectedness of critical infrastructure amplify these vulnerabilities, making the consequences of policy failures increasingly severe. He explains that manufacturers prioritize cost-savings over security. This leaves devices lacking the quality assurance needed (Matthews, 2017). And the lack of penalties for insecure products means companies have no incentive to change posture (Tjahja, 2022). Hiller et al. explain that existing regulatory frameworks are siloed by sector, leading to inconsistent oversight.
Case Analysis
Hiller et al. document how each year brings record-breaking cyberattacks. The authors argue that negative externalities and information asymmetries lead to chronic underinvestment in cybersecurity. Schneier suggests that the rapid proliferation of IoT devices has expanded the attack vectors for malicious actors. Duarte states that in 2025 the worldwide sum of connected IoT devices will reach 30.9 B (2024). Internet+ interconnectedness enables vulnerabilities to cascade and amplify, Schneier adds; and as the number of devices grows, risk grows exponentially.
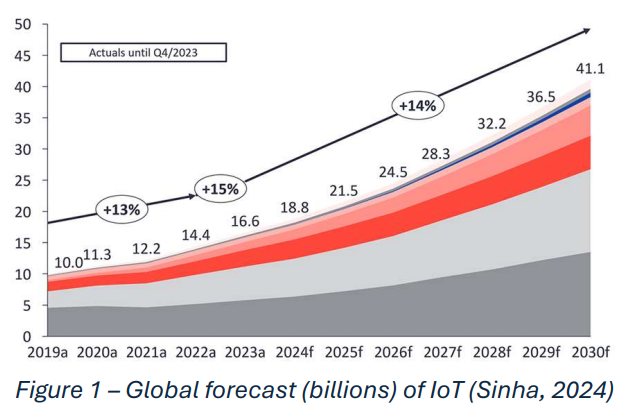
However, at the time of Schneier’s writing, Gartner’s 2020 projection of connected IoT devices reaching 20.5 B was an overestimation. Sinha reported only 11.3 B devices (2024). Despite this, Schneier’s concern is still warranted. The core problem identified by Hiller et al. is the systemic insecurity inherent in the modern digital ecosystem. Schneier suggests that IoT devices are often rushed to market with security considerations lacking. Key issues include the absence of industry incentives to prioritize security, insuƯicient regulatory oversight, and a gap in consumer awareness. These factors collectively contribute to an environment where vulnerabilities in everyday devices can be exploited to jeopardize physical safety and national security.
"A rational CEO will choose to save money [on security] or spend it on new features to compete in the market... most of the costs of insecurity will be borne by other parties" (p. 124). Schneier frames this as a "Prisoner’s Dilemma," where companies avoid security costs to maintain competitive pricing, despite the systemic risks. The market favors rapid development and cost savings over robust security (Davy, et al., 2022). Meanwhile, consumers are ill-equipped to demand better protection. Moreso, Hiller et al. explain that the absence of mandatory security standards and oversight exacerbates these issues.
Hiller et al. use real-world incidents and plausible scenarios to illustrate the dangers, including weak default passwords (Naprys, 2025), delayed software updates (Islam, 2023), and omitting encryption for sensitive data (ESG, 2024). Additionally, Schneier portrays his hypothetical “click here to kill everybody” scenario, where a hacked bioprinter created a lethal virus. These examples highlight that IoT insecurity is not just a technical issue, but a societal risk with potentially global consequences.
Alternative Solutions
The alternatives to Hiller et al.’s cybersecurity challenges are as follows. One option is the adoption of voluntary industry standards. These must quickly adapt to technological changes and impose less regulatory burden on manufacturers (Goldstein, 2018). However, Schneier stresses that their eƯectiveness is limited. He illustrates historic examples of manufacturers ignoring security best practices (e.g., Jeep’s delayed patch, D-Link’s deceptive trade practices). Pardis et al. suggests another approach involving increasing consumer awareness (2020). This can empower consumers to make safer choices and raise public pressure on manufacturers (Xiao, 2021). However, the technical complexity of IoT and the information asymmetry thereof makes it diƯicult for consumers to assess device security, warns Schneier. “This asymmetry makes deterrence more diƯicult” (p. 92).
Technical solutions directly address vulnerabilities and can be incrementally adopted by manufacturers. This may involve implementing better encryption and secure coding practices. While these measures are important, Schneier suggests that their adoption is uneven across the industry. Moreso, they cannot resolve the broader systemic issues, he includes. Additionally, Kavinsky explains that the IoT global supply chains and data flows complicate regulation enforcement (2023). Therefore, Schneier suggests mandatory security standards (instead of voluntary) which oƯer a comprehensive, consistent solution where manufacturers are compelled to comply. Nevertheless, regulatory approaches may be slow to adapt to rapid technological change. Moreso, manufacturers may be forced to raise prices for consumers and sacrifice innovation (Emami-Naeini, et al., 2020).
The primary solution advanced by Hiller et al. is an incentive-based tax policy toolkit that includes both tax credits for positive cybersecurity investments and penalties for underinvestment, tailored to entity size and industry. While voluntary standards and consumer awareness campaigns are discussed as alternatives, both the article and Schneier’s work highlight their limitations in the face of complex, evolving threats (Wolf, 2019). Schneier’s advocacy for mandatory standards and product liability complements the article’s call for policy tools that realign private sector incentives with the public good.
Conclusion
The “carrots and sticks” incentive-based framework outlined by Hiller et al. presents a practical and balanced solution to the chronic underinvestment in cybersecurity. By combining tax credits for proactive security measures with penalties for noncompliance, this approach directly addresses the market failures and misaligned incentives that have left many small and medium-sized businesses of whom are vulnerable to attack.
Schneier’s examples of IoT and infrastructure breaches reinforce the urgency of adopting such systemic reforms. While voluntary standards and consumer education remain helpful, both Hiller et al. and Schneier demonstrate these alone are insuƯicient for today’s rapidly evolving cyber risks. Ultimately, the “carrots and sticks” strategy oƯers a promising path to realign incentives, foster accountability, and build a more resilient digital ecosystem.
Bibliography
Davy, T., Dholiwar, V., Carr, M., Maidment, D., Costante, E., & Eaves, S. (2022, 1 1). The IoT Industry Action Plan to Reduce the Cost of Security. Retrieved from psacertified.org: https://www.psacertified.org/app/uploads/2022/08/Confidence_to_Create_Advisor y_Paper_PSA_Certified-1-compressed.pdf
Duarte, F. (2024, 2 19). Number of IoT Devices (2024). Retrieved from explodingtopics.com: https://explodingtopics.com/blog/number-of-iot-devices
Emami-Naeini, P., Dheenadhayalan, J., Agarwal, Y., Cranor, L. F., CMU, & CyLab. (2020). Which Privacy and Security Attributes Most Impact Consumers’ Risk. FTC PrivacyCon CyLab. Pittsburg, PA: Carnegie Mellon University, CyLab.
ESG. (2024). ESG Report Operationalizing Encryption and Key Management. fortanix.com. Retrieved from https://resources.fortanix.com/esg-report-operationalizingencryption-and-key-management
Goldstein, P. (2018, 3 27). Will There Be a Government Standard for IoT Security? Retrieved from fedtechmagazine.com: https://fedtechmagazine.com/article/2018/03/willthere-be-government-standard-iot-security
Hiller, J., Kisska-Schulze, K., & Shackelford, S. (2024). Cybersecurity Carrots and Sticks. American Business Law Journal 61, 5-29.
Islam, M. A. (2023, 5 23). The Risks of Neglecting Software Maintenance and Updates. Retrieved from devs-core.com/: https://devs-core.com/the-risks-of-neglectingsoftware-maintenance-and-updates/
Kavinsky, M. (2023, 11 13). The Regulatory Landscape for IoT: Navigating the Complexities of a Connected World. Retrieved from iotbusinessnews.com: https://iotbusinessnews.com/2023/11/13/84084-the-regulatory-landscape-for-iotnavigating-the-complexities-of-a-connected-world/
Matthews, A. (2017, 1 12). Challenges, solutions and security needs in IoT business plans. Retrieved from electronicspecifier.com: https://www.electronicspecifier.com/products/iot/challenges-solutions-andsecurity-needs-in-iot-business-plans
Naprys, E. (2025, 5 13). 19 billion leaked passwords reveal deepening crisis: lazy, reused, and stolen. Retrieved from cybernews.com: https://cybernews.com/security/password-leak-study-unveils-2025-trends-reusedand-lazy/
Schneier, B. (2018). Click Here to Kill Everybody: Security and Survival in a Hyperconnected World (1st Edition). W. W. Norton & Company. Retrieved from https://www.amazon.com/Click-Here-Kill-Everybody-Hyperconnected/dp/0393608883#detailBullets_feature_div
Sinha, S. (2024, 9 3). State of IoT 2024: Number of connected IoT devices growing 13% to 18.8 billion globally. Retrieved from iot-analytics.com: https://iotanalytics.com/number-connected-iot-devices/
Tjahja, N. (2022, 12 29). Are companies responsible for the security of their digital services and products, and to what extent? Retrieved from diplomacy.edu: https://www.diplomacy.edu/blog/are-companies-responsible-for-the-security-oftheir-digital-services-and-products-and-to-what-extent/
Wolf, C. (2019, 7 1). Book Review: Click Here to Kill Everybody. Retrieved from asisonline.org: https://www.asisonline.org/security-managementmagazine/articles/2019/07/book-review-click-here-to-kill-everybody/
Xiao, Q. (2021). Understanding the asymmetric perceptions of smartphone security from security feature perspective: A comparative study. Telematics and Informatics Volume 58, 101535.
Emerging Technologies Literature Review
James V. Tarlton
5/4/2025
Abstract
This paper presents a comparative analysis of three influential works—Azeem Azhar’s The Exponential Age (2021), Adrian Daub’s What Tech Calls Thinking (2020), and Bernard Henri Lévy’s The Virus in the Age of Madness (2020). The paper interrogate how rapid technological, ideological, and biological change is reshaping society. Additionally, intersections between these works and the philosophies of political scientist Dr. George Friedman are recognized. Azhar explores society’s exponential gap between fast innovation and slow adoption, which parallels Friedmans American institutional and industrial cycles. Daub dissects Silicon Valley’s self-mythologizing and selective amnesia, which parallels Friedman’s observation of how ideology has shaped institutions that prioritize capital over democracy. Lévy critiques the elevation of medical authority and the reduction of liberties during the COVID-19 pandemic, which parallels Friedman’s critique of a disconnected technocracy. Through examination of these intersections and divergent arguments, this study reveals a shared concern about the dangers of unchecked power and the erosion of agency, ethical responsibility, and democratic oversight in times of disruption and crisis.
Introduction
Society has recently entered a period of rapid technological, ideological, and biological change. Innovations are reshaping society at an exponential pace. However, longstanding institutions, legal frameworks, and cultural norms are struggling to keep up, creating what Azeem Azhar terms the “exponential gap.” This widening divide between technological progress and societal adaptation has fueled polarization, inequality, and concentrated power. Meanwhile, the technology industry’s self-mythologizing and selective amnesia serves to obscure historical context, limit critical discourse, and shield companies from accountability, as Adrian Daub argues. Moreso, COVID-19 has exposed vulnerabilities of contemporary society, with BernardHenri Lévy warning against unchecked medical authority, and erosion of democratic debate and civil liberties.
This paper offers a comparative analysis of The Exponential Age by Azeem Azhar (2021), What Tech Calls Thinking by Dr. Adrian Daub (2020), and The Virus in the Age of Madness by Bernard-Henri Lévy (2020), examining how each work interrogates the impact of rapid changes in societal structures, individual agency, and the balance of power. By exploring intersections and divergences in their critiques, this study highlights challenges and ethical dilemmas facing society. Ultimately, these works converge for renewed engagement, ethical vigilance, and collective action to ensure benefits of progress are shared and that democracy and dignity are preserved amidst disruption and crisis. Additional intersections between these works and Geroge Friedman’s socioeconomic philosophy are explored. Friedman’s 80-year institutional and 50-year industrial cycles state that America undergoes political and socioeconomic transformations, respectively (2020).
Analysis and Overview of the Exponential Age
The central themes of The Exponential Age (2021) revolve around the exceptional pace of technological advancement and acute societal challenges thereof. The book introduces the concept of the "exponential gap," (p. 16) which describes rapidly evolving technologies and society's inability to adapt its institutions, laws, and cultural norms. The gap is revealed in political polarization, rising inequality, and unchecked corporate power.
The central themes of The Exponential Age (2021) revolve around the exceptional pace of technological advancement and acute societal challenges thereof. The book introduces the concept of the "exponential gap," (p. 16) which describes rapidly evolving technologies and society's inability to adapt its institutions, laws, and cultural norms. The gap is revealed in political polarization, rising inequality, and unchecked corporate power.
Moreso, Azhar highlights how traditional linear thinking and institutional "path dependence" (p. 110) leave societies ill-equipped for exponential change. He explains that the repercussions of this are that it results in “institutional lag and cultural lag” (p. 87), as seen in the rise of the gig economy, data breaches, and pandemic response.
The Exponential Gap
In Wired (2021), Azhar suggested the gap is created by two forces—"the inherent difficulty of making predictions” and “the inherent slowness of institutional change” (para. 41). Business dynamics have shifted, with big-tech companies leveraging network effects, intangible assets, and platform models to achieve unprecedented scale and dominance. Notably, at the expense of smaller producers and economic dynamism, he adds. Additionally, he argues that these firms exploit global tax loopholes and challenge traditional antitrust frameworks. Thus, affecting labor compensation through shifted tax burdens (Doyle, Carlos, & Serrato, 2024). This, in concert with automation, negatively impacts labor markets (Holzer, 2022). However, Azhar explains that the rise of gig work has brought forth the benefit of increased work flexibility. Though, this type of work is associated with insecurity and inequality; thus, new approaches to labor rights and protections are needed, per NBER (2025).
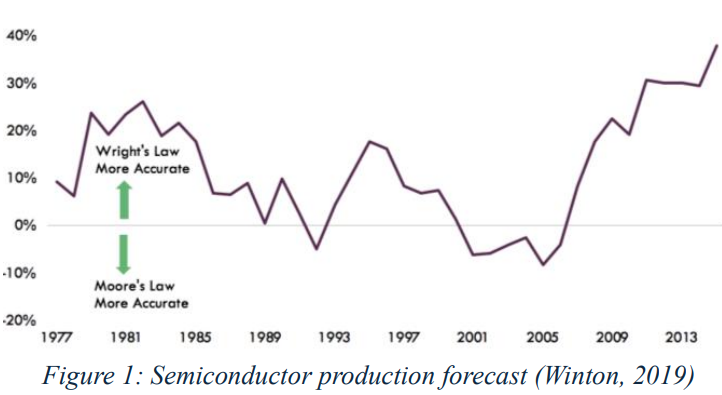
Wright’s Law vs Moore’s Law
Drivers of Azhar’s exponentiality include global supply chains and freemarket economics. Azhar suggests that the free-market helped drive globalization; and, in turn, globalization helped drive the Exponential Age. He suggests that the Exponential Age can be traced back to the early 1900s with Theodore P. Wright’s analysis of airplane production costs (1936). In fact, experts indicate that Wright’s Law more accurately describes technological evolution when compared to Moore’s Law (McCormick, 2012) (Johnson, 2013) (Winton, 2019) (Figure 1).
The Exponential Gap vs Hype Gap
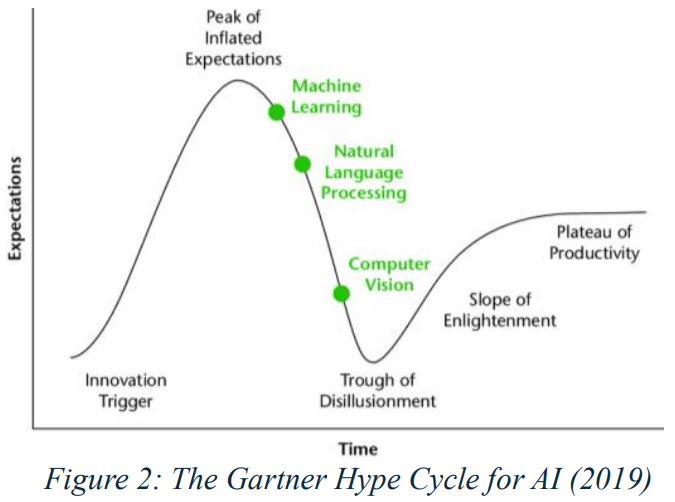
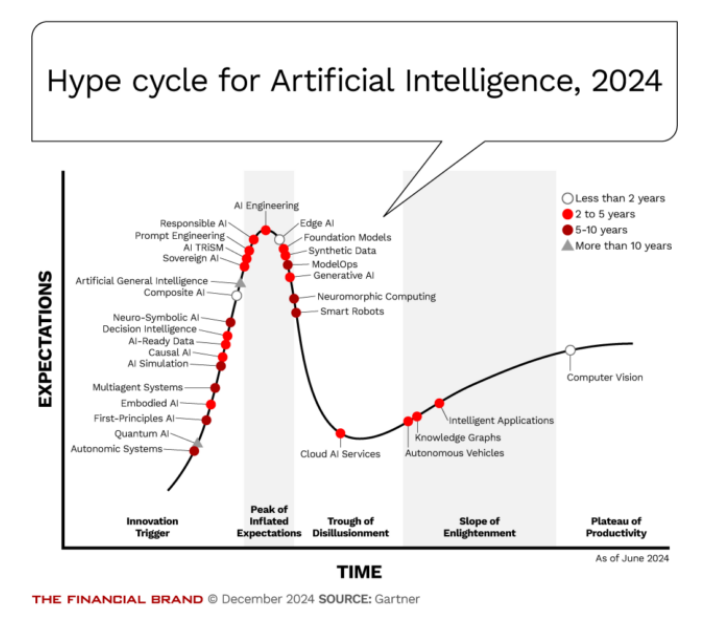
The “Tech Hype Gap” describes when anticipation about a technology precedes its actual usage. Moreso, it highlights the negative social impact of marketing outpacing actual progress (Davis, 2019). This gap is based off the “Gartner Hype Cycle,” which describes the maturity and adoption of technologies over time (Fenn & Linden, 2003). Moreso, Fenn and Raskino explain that overly optimistic expectations can lead to discontent or backlash if a technology does not “live up to the hype” (2008). While the Gartner Hype Cycle originates from overly optimistic marketing claims, particularly for AI (2019) (Figure 2) (Appendix A), the Exponential Gap is caused by technology growth, causing market disruption and societal inequalities. For instance, market disruption is seen through the emergence of online retailers like Amazon displacing brick-and-mortars stores. Moreso, gig work displacing official work exacerbates income inequality (Sankararaman, 2024).
Globalization
The world has entered a third phase of globalization which involves sophisticated, digitized supply chains (Friedman T. , 2005). However, Ahar suggests that, geopolitically, the world is becoming "spiky," with innovation and prosperity concentrated throughout urban centers of wealthy nations. Modern technologies enable local production and fragment global networks into "splinternets" (pp. 206 – 235). In its inception, the Internet was distinctly American but always promised a borderless future. However, cybersecurity, disinformation, and digital warfare have exposed vulnerabilities to government agencies, requiring new norms, cooperation, and resilience in the face of rapidly evolving threats.
The Four Broad Domains
Computing
The computing domain is realizing new GPTs like Artificial Intelligence (AI), Cloud Computing, and Quantum Computing. Therefore, Azhar suggests that new frameworks are needed to ease their transitions. Gartner’s Hype Cycle helps avoid inflated expectations and disillusionment of AI (Coshow, 2024). DevSecOps, an IT project management methodology, avoids vulnerabilities to cybersecurity attacks that organizations might face in the cloud (NIST, 2022). The Quantum Computing Cybersecurity Preparedness Act (2022) ensures resilience of information systems in a post-quantum cryptography Internet (Sanzeri, 2023).
Energy
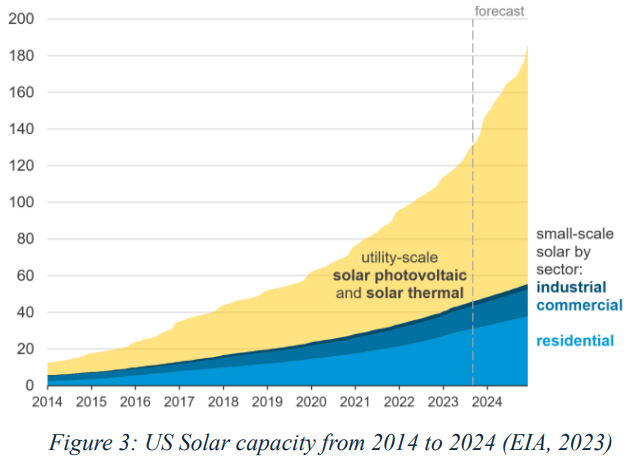
According to a Rockwell Automation survey, energy management is the top sustainability concern for organizations (2025). The energy domain is emerging with new GPTs like next-gen renewables, batteries, and nuclear reactors (Chu & Tarazano, 2025). The solar panel first appeared at Bell Labs in the 1950s, with low efficiency. However, continuous advancements in efficiency and affordability realize a wider adoption (EIA, 2023) (Figure 3). Next generation battery technologies (i.e., sodium-ion, solid-state), offering faster charging and more capacity than their lithium-ion counterparts (DOE, 2025), make electronic vehicles (EVs) safer and more efficient—thus more enticing to consumers (Reuters, 2025). Improvements to nuclear reactor design (Barbarino, 2022) promise advancements in energy production, waste management, and overall societal benefits (WNA, 2021). For instance, experts suggest nuclear power is key to meet the future demands of computational power for AI and data center processing (Calma, 2023) (Browne, 2024).
Biology
DNA synthesis, genomics, and biomanufacturing are novel GPTs in the biology domain highlighting revolutionary evolution in the exponential age. Recent advances in automated DNA synthesis enable the creation of new DNA sequences for various applications. Patents surrounding DNA Synthesis reached approximately 472 thousand filings in 2023. This suggests wide scientific community adoption and use (Wellspring, 2024). Regarding genomics, long-read sequencing techniques (e.g., Oxford Nanopore) offer unprecedented accuracy and accessibility. For instance, the SmidgION brings laboratory-grade sequencing to mobile devices (Wang, et al., 2021). Industry 4.0 and the Industrial Internet of Things (IIoT) are key determinants in the future state of biomanufacturing (Dikicioglu & Borgosz, 2024). Concepts like soft sensors aid in the digitization of bioprocessing (Rathore, Nikita, & Jesubalan, 2022).
Manufacturing
Smart manufacturing, additive manufacturing, and cloud-based supply chains are revolutionizing manufacturing for organizations. Worldwide, companies continuously increase their technology budgets to integrate smart manufacturing equipment into their factories (Rockwell Automation, 2025). Additive manufacturing, or 3D printing, is enabling manufacturers to become more agile by harnessing rapid prototyping of new designs and concepts (Chen & Lin, 2019). Additionally, this approach allows manufacturers to explore new material science breakthroughs with varieties of additive polymers (King, 2022). Regarding cloud-based supply chains, GenAI integrations are the top technology investment for manufacturing companies (Gartner, 2025).
Institutional and Cultural Lag
Azhar defines institutional and cultural lag in terms of the organizational and societal implications they can have such as political division, inequality, and unchecked power. Similarly, the ends of George Friedman’s cycles (i.e., 80-year institutional, 50-year industrial), each predict political and economic disruption, respectively (2020). The late 2020s are unique in that these 80- and 50-year cycles will converge amid the “exponential age.”
Prior to The Great Depression, William Ogburn observed lag associated with the introduction of industrial machinery and automobiles (1922). Rick Maurer points to other examples of institutional and cultural lag within the information technology realm including resistance to change and digital literacy, respectively (2010). In fact, according to a Gartner survey, 80% of all data breaches within organizations are caused by misconfigured systems and 99% of cloud failures are attributed to human error (Panetta, 2019). This suggests a knowledge gap (or lag) in workforces throughout organizations (Chaudhary, 2023).
Implications
Azhar’s “exponential gap” reflects the widening divide Friedman describes in his socioeconomic cycles. Both warn that unchecked, exponential growth risk overconsumption, systemic instability, and further concentration of power. However, he also emphasizes that society can shape these outcomes through deliberate choices, updated policies, and new institutions focused on transparency, digital rights, and building shared digital commons. From an IT perspective, if an organization lags, it risks operational inefficiencies (e.g., outdated software, hindered automation), financial risks (e.g., accounting compliance issues, lost opportunities), and security risks (e.g., malware, data breaches) (Byrd, 2024). Finally, Lauren Arcuri suggests that technological advancements have contributed declining birth rates (2019).
Remedies
Azhar calls for radical thinking and collective action to bridge the exponential gap, harnessing technological change for the common good and ensuring that the benefits of the Exponential Age are widely shared. For example, Florida Governor DeSantis’s Digital Bill of Rights, protects Floridians from the overreach and surveillance of tech giants (FedSoc, 2023). Regarding IT lag, federal agencies housing sensitive data are hesitant to move to the cloud despite their software vendors urging them to do so (Hanna, 2023) (Chao, 2024). To aid in this predicament, the National Institute of Standards and Technologies (NIST) designed the Federal Risk and Authorization Management Program (FedRAMP) framework in alignment with Federal Information Security Modernization Act (FISMA) to ensure US federal agencies can securely use cloud technologies. FedRAMP laid a foundation for companies and other governments to help reduce the risk of data breaches and cyber threats (Blokdyk, 2021). FedRAMP coupled with the DevSecOps IT project management and deployment methodology helps ensure that cloudbased information systems are not prone to vulnerabilities (Arshad, 2023). Regarding declining birth rates, Dr. Karen Guzzo suggests institutionalized pronatalist tactics such as tax benefits or subsidies (2025).
Analysis and Overview of What Tech Calls Thinking
The central themes of Adrian Daub’s What Tech Calls Thinking (2020) revolves around how the technology industry constructs self-referential mythology and worldview by reframing old ideas, selectively forgetting history, and promoting false narratives. Daub argues that these tactics confine critical dialogue and disenfranchise relevant experience. Moreso, he explains that the industry’s embrace of technological determinism serves to justify ethically questionable practices and to minimize accountability.
Mythology and Worldview Construction in Tech
Daub suggests that the technology industry cultivates self-referential mythology by reframing historical ideas as novel where “the myth of precariousness persist[s]” (p. 12). This process involves selectively erasing context to position technological development as an inevitable force rather than a socially contingent process. By obscuring precedents (e.g.,19th century industrialism, 1960s counterculture) technology leaders present governance and labor challenges as unprecedented. They then proceed to stifle meaningful dialogue with critics who draw parallels to past societal shifts, Daub explains. For instance, work by Thiel and Sack at Stanford (1998) explores the groupthink mentality they observed in academia. However, this continues to be observed (Wooldridge, 2023) (Blease, 2023).
Selective Historical Amnesia
 Daub suggests that selective amnesia observed within the technology industry enables
companies to dismiss regulatory concerns and ethical critiques. He highlights gig economy
worker rights as clashes between modern tech models and old labor laws, like 20th-century
workplace protection struggles. Moreso, the emergence of online riding sharing platforms has
decreased employment and earnings within the taxi industry, per NBER (2025) and Schneider
(2019) (Figure 4). Additionally, “[c]oding went from being clerical busywork done by women to
a well-paid profession dominated by men” (p. 8). Also, Daub suggests that the historical
precedents for monopolistic practices and privacy encroachments have become minimized.
Technology companies are positioning themselves in uncharted territory; therefore, Daub
suggests the need for new frameworks. Likewise, Kristie Lam of UC San Franciso College
of Law suggests the adoption of antitrust frameworks to ensure data collection practices
no longer violate user privacy, e.g., Klein v. Facebook (2022), (Lam, 2024).
Daub suggests that selective amnesia observed within the technology industry enables
companies to dismiss regulatory concerns and ethical critiques. He highlights gig economy
worker rights as clashes between modern tech models and old labor laws, like 20th-century
workplace protection struggles. Moreso, the emergence of online riding sharing platforms has
decreased employment and earnings within the taxi industry, per NBER (2025) and Schneider
(2019) (Figure 4). Additionally, “[c]oding went from being clerical busywork done by women to
a well-paid profession dominated by men” (p. 8). Also, Daub suggests that the historical
precedents for monopolistic practices and privacy encroachments have become minimized.
Technology companies are positioning themselves in uncharted territory; therefore, Daub
suggests the need for new frameworks. Likewise, Kristie Lam of UC San Franciso College
of Law suggests the adoption of antitrust frameworks to ensure data collection practices
no longer violate user privacy, e.g., Klein v. Facebook (2022), (Lam, 2024).
Technological Determinism as Ideology
Per work by early 20th century sociologist Thorstein Veblen, technological determinism is the belief that technological advancement is inevitable and outside human control. Moreso, it is the belief that tools dictate societal outcomes (McLuhan, 1964). The technology industry’s embrace of technological determinism serves as prophecy and justification. For instance, framing technological advancements (e.g., AI, blockchain) as autonomous forces, technology executives deflect accountability, arguing they merely respond to inevitable progress. This worldview underpins arguments against regulation and ethical oversight, suggests Daub.
However, in a subcommittee hearing regarding the cybersecurity implications of a lacking AI posture within government agencies, the Office of Management and Budget (OMB) notably argued that innovation must not be stifled (2023). Industry experts recommend AI powered risk analysis software to stay secure in cyberspace (IBM) (Cisco). The fact that AI must be fought with AI brings forth a conundrum to governments and organizations (Humble, 2024).
Linguistic Framing and Power Dynamics
Because of its influence on human advancement, innovation is complicated to legislate. Regarding linguistics and dynamics, Daub suggests that “neuro-linguistic programming remains influential today” (p. 144). He states rhetoric behind certain buzzwords (e.g., disruption, scale) launder extractive practices as revolutionary altruism. He explains that these terms create a linguistic ecosystem where criticism becomes semantically impossible to oppose. This is like President Trump’s rhetorical use of “common sense” to establish dichotomy with political opponents (Wodajo, 2025). Whether or not ulterior motives are at play in these accounts, Daub brings forth a relevant conversation. This parallels Friedman’s observation of how neoliberalism has shaped economic and political institutions in ways that prioritize capital over democratic governance (Kottász, 2023).
Repurposing Traditions
Daub suggests that “innovative” technology concepts are recycled versions of older concepts. For instance, he argues that the tech “dropout” myth repackages frontier individualism, masking the role of privilege, e.g., family wealth, elite networks. He explains that these factors enable risk-taking that less privileged students do not have. “It’s worth keeping this sense of dropping out in mind when one considers the mythology of famous tech industry college dropouts” (p. 29), he adds. Gap years (or dropping out altogether) in university enable students to venture into entrepreneurship and explore creativity. Therefore, Michael B. Horn, of the Chistensen Institute, argues that gap years should be made available to all students because of the benefits incurred, i.e., career exploration, personal growth, cultural experiences, reduced burnout (2020).
Commodified Self-Help
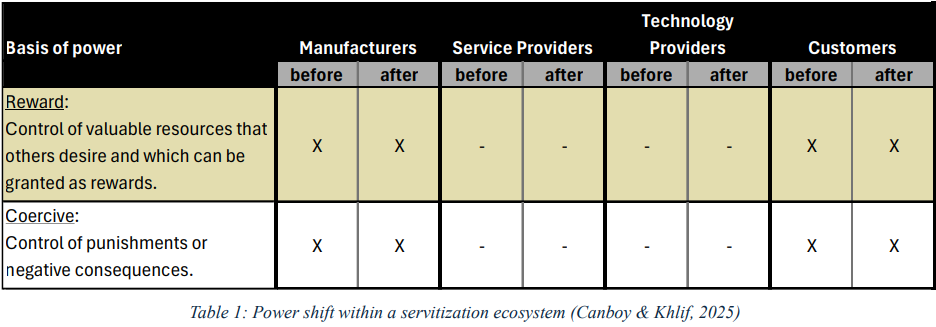
Daub observes that productivity-tracking apps centralize power by being commodified into marketing programs. For instance, a study by Canboy & Khlif (2025) observes the advancing power dynamics across companies that offer productivity-tracking software within servitization ecosystems, e.g., Google, Apple. The authors suggest that servitization can negatively impact customers and manufacturers (Table 1). Servitization is a paradigm shift exposing manufacturers to new revenue streams; however, it can reduce customer ownership and increase customer dependency (Zhang & Banerji, 2017).
Dominance Amongst Platforms
Regarding platform dominance, Daub argues that Silicon Valley has focused on McLuhan-inspired “medium over message” (2001). He explains that this is observed in social media platforms that devalue content. For instance, some experts suggest YouTube’s recommendation algorithm is left-leaning (Ibrahim, et al., 2023) (Dolan, 2023), while others suggest the opposite (Iyer, 2023). By this sentiment, Daub alludes to Marshall McLuhan’s work on cultural transformations and the impact of mass media on societal norms (1964). Other authors’ findings share similar results (Euchner, 2021) (Cole, 2020).
Manipulation of Labor Laws
Daub suggests that social media firms avoid compensating their content creators by categorizing their work as hobbyism. Section 230 of the Communications Decency Act further enables this cost avoidance by absolving platforms of responsibility for hosted content, despite algorithmic amplification of biased or harmful material. Alan Rozenshtein suggests that ambiguities within Section 230 allow platforms to bypass restrictions (2023). Moritz Schramm raises similar concerns about the European Union’s Digital Services Act, arguing that while it aims to set global regulatory standards, it actually grants significant discretion to private entities in its implementation in the pursuit of globalization (2025).
Philosophical Underpinnings and Contradictions
Daub alludes to Ayn Rand’s philosophy of heroic individualism as a staple ideal that permeates technology culture. He suggests that this ideal aestheticizes overworking as passion. Leonard Peikoff shares similar sentiments, suggesting that objectivism frames corporate growth as a moral virtue (1993). Daub explains that this ethos surfaces in founder narratives that celebrate “genius” visionaries while ignoring systemic advantages. For example, the gig economy exemplifies this contradiction, rebranding precarious work as entrepreneurial freedom. Moreso, Daub suggests that Silicon Valley’s celebration of failure, e.g., “fail fast and then iterate” (p. 144), obscures its uneven consequences. For instance, while privileged founders frame setbacks as learning opportunities, marginalized workers face disproportionate fallout from algorithmic layoffs or startup collapses (Faber, Williams, & Skinta, 2024). This selective framing ignores the safety nets (e.g., venture capital, familial wealth, telework capabilities) of privileged workers. For instance, the impact of COVID-19 on labor markets further epitomizes this notion regarding the inequality between white- and blue-collar workers (BLS, 2022).
Open Communication and Its Discontents
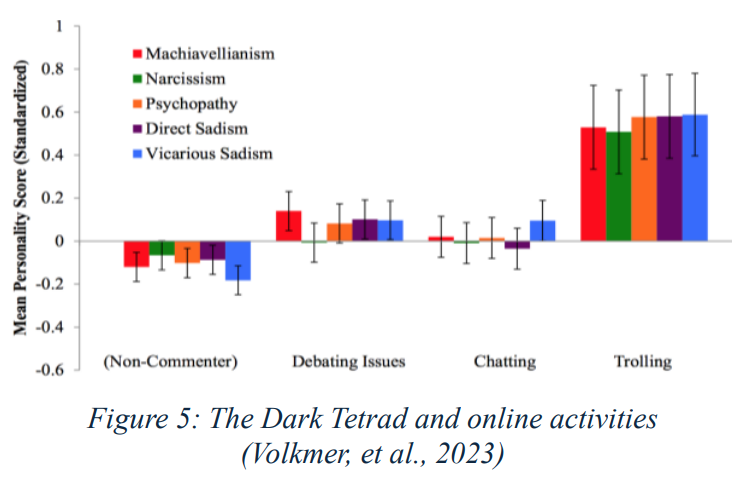
Despite rhetoric about democratizing discourse, engagement-driven platforms often incentivize polarization, explains Daub. He states that tools designed for “connection” frequently amplify abuse and misinformation. For instance, clinical experts suggest that social media causes depression amongst children (Lin, et al., 2016 ) (Miller, 2025). Additionally, Internet trolling emerges as both a byproduct and instrument of this system, describes Volkmer, et al. (2023). They explain that malicious users weaponize free speech to harass others. Furthermore, they suggest a strong correlation (Figure 5) between trolling and the “Dark Terad” of personality (i.e., Machiavellianism, narcissism, psychopathy, sadism) by Buckles, et al. (2013).
Mimetic Desire and Manufactured Conflict
Daub recalls Peter Thiel’s adoption of René Girard’s mimetic theory which frames human desire as imitative. Douglas Green explains how Girad's mimetic theory, when applied to business applications, can forecast consumer behavior and market trends (2025). However, Daub reveals how tech giants manipulate narratives for competitive gain. For instance, by portraying markets as arenas of existential rivalry, technology executives attempt to justify monopolistic practices while minimizing criticisms. This victimhood narrative reinforces Silicon Valley’s self- image as a persecuted visionary class. In fact, Deborah Perry Piscione relates this “ingenuity” to political dysfunction (2013).
Analysis and Overview of Virus in the Age of Madness
Bernard-Henri Lévy’s Virus in the Age of Madness (2020) offers a critique of the societal and governmental responses to the COVID-19 pandemic worldwide. Lévy argues that anxiety and authoritarianism threaten to corrode democratic values, ethical responsibility, and human connection. He also offers insight into the geopolitical dynamics surrounding the pandemic response. Additionally, he calls for a revival of civic discourse and a rejection of reductive views of human life by dissecting the intersection of medical authority, philosophy, and politics.
The Rise of Medical Authority and Democratic Erosion
Medical Gaze and Modern Implications
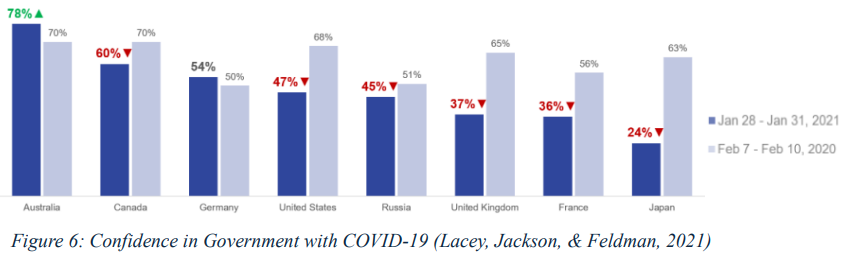
Lévy draws on Michel Foucault’s concept of the “medical gaze” to analyze how the pandemic amplified the influence of doctors and health experts. Foucault discovered perceived connections between knowledge and power within medical industry, arguing that “those in power set the agenda” (1994). Lévy observed this during COVID-19, which led to marginalizing political judgment and democratic oversight. He warns that unchecked authority risks repeating historical abuses (e.g., eugenics) by prioritizing biological survival over civil liberties. Similarly, George Friedman critiques technocrats, disconnected from practical realities, leading to institutional failures in balancing health measures with underlying economic and social costs (2021). In a study analyzing governmental response to COVID, Lacey, Jackson, & Feldman observed a degradation in citizens’ confidence (2021) (Figure 6), implying dissatisfaction.
The Fragility of Scientific Consensus
Contrary to portrayals of science as monolithic, alluded in Griffin Trotter’s journal article about COVID-19 and the “Authority of Science” (2023), Lévy emphasizes its inherent uncertainty and internal conflicts. He argues that treating science as an infallible authority stifles debate, allowing a technocracy to impose policies without transparency or accountability. Friedman suggests that technocrats “live their lives abstractly” and “all [their] problems are intellectual” (2020) (p. 156), which underscores Lévy’s concern about unchecked authority.
Rejecting Romanticization of the Pandemic
Moral and Redemptive Narratives
Lévy criticizes narratives that attribute moral lessons or divine purpose to the virus, calling them intellectually misguided and insensitive to human suffering. He asserts that viruses lack intentionality, and pandemics do not inherently convey virtue or cosmic messages. Likewise, Trotter argues that moral and political stances cannot be derived solely from objective facts (2023). Consequently, this limitation has motivated scientists and policymakers to engage in actions and make statements that undermine the credibility of science, he concludes.
Pragmatism Over Utopianism
Lévy’s philosophy rejects extensive social blueprints and future-oriented idealism in favor of pragmatic, ethical responses to injustice and a defense of liberty (Gardels, 2021). Throughout the book, Lévy advocates for rational, pragmatic debates about pandemic responses, urging societies to weigh concrete costs against the benefits of restrictive measures. These costs may include economic collapse or mental health crises. Lévy rejects utopian visions of societal rebirth, e.g., Fernando, et al. (2022), Yoshihisa & Fernando (2020). On the contrary, Lévy insists that solutions must address immediate human needs rather than broad, abstract ideals.
Critique of Lockdown as Spiritual Retreat
Privilege and Disconnection
Lévy exposes the romanticization of lockdowns as opportunities for self-improvement or spiritual growth, arguing that this view reflects privilege and ignores the struggles of those in poverty, abusive households, or solitary confinement. For marginalized groups, including people with disabilities, isolation exacerbates existing vulnerabilities (Hwang, Rabheru, Peisah, Reichman, & Ikeda, 2020). Critics of Lévy’s work argue that “[i]t can be, at times, difficult to read” (Huminski, 2020) (para. 16) and that he claims the “responses to the coronavirus have been a matter of political psychosis” (McLemee, 2020) (para. 7).
Philosophical Foundations of Engagement
Drawing on existentialist and humanist traditions, Lévy contends that fulfillment arises from engagement with others, not withdrawal. While it may be medically necessary, social distancing risks normalizing alienation and weakening the ethical bonds that sustain communities (Zhu, Zhang, Zhou, Li, & Yang, 2021). Moreso, Lévy depicts a shift from a social contract to a “life contract” that trades liberties for security. This shift is further described as being grounded in mutual rights and responsibilities. He also questions whether this transition is temporary or a precursor to a surveillance-driven future where bodily safety eclipses intellectual, cultural, and spiritual pursuits. Finally, Lévy concludes with a plea to prioritize humanistic values (i.e., compassion, solidarity, intellectual curiosity) over fear-driven conformity. He envisions a future where societies embrace virtues (i.e., risk, complexity, global responsibility) and reject “madness” of authoritarianism.
Global Isolationism and Abandoned Solidarity
Retreat from Global Engagement
 Lévy laments how Western societies turned inward
during the pandemic, neglecting ever-present global crises
such as poverty. He argues that this isolationism contradicts
the interconnected reality of modern life and undermines
moral obligations to vulnerable populations. Moreso, AMA
Journal of Ethics researchers suggest that people with disabled
embodiment were particularly isolated from pandemic-induced confinement (Atkins & Das,
2022). Additionally, he suggests that the pandemic accelerated the adoption of digital
surveillance tools. Alongside this observation, a Deloitte survey found organizations’ technology
budgets increase amid the pandemic (2021) (Figure 7). By governments normalizing intrusions
into private life under the guise of public health, Lévy warns that such measures could outlast the
crisis, enabling perpetual authoritarianism under the banner of safety. This parallels prior
concerns about the USA Patriot Act’s impact on privacy, e.g., Pattat (2023), Li (2021).
Lévy laments how Western societies turned inward
during the pandemic, neglecting ever-present global crises
such as poverty. He argues that this isolationism contradicts
the interconnected reality of modern life and undermines
moral obligations to vulnerable populations. Moreso, AMA
Journal of Ethics researchers suggest that people with disabled
embodiment were particularly isolated from pandemic-induced confinement (Atkins & Das,
2022). Additionally, he suggests that the pandemic accelerated the adoption of digital
surveillance tools. Alongside this observation, a Deloitte survey found organizations’ technology
budgets increase amid the pandemic (2021) (Figure 7). By governments normalizing intrusions
into private life under the guise of public health, Lévy warns that such measures could outlast the
crisis, enabling perpetual authoritarianism under the banner of safety. This parallels prior
concerns about the USA Patriot Act’s impact on privacy, e.g., Pattat (2023), Li (2021).
Sanitized Society vs. Human Condition
The book contrasts risk-averse doctrine with the human condition, which thrives on connection and courage. Lévy warns that excessive focus on physical safety jeopardizes creating a sterile, dehumanized world. Lévy urges society to resist reducing life to mere survival, advocating instead for democratic renewal rooted in ethical vigilance. This requires challenging medical and technological overreach while preserving spaces for dissent and debate. Also noteworthy, in a society with an already decreasing birth-rate, COVID-19 further exacerbated the decline (Kearney & Levine, 2023).
Point-Counterpoint
The three books—The Exponential Age (2021) by Azeem Azhar, What Tech Calls Thinking (2020) by Adrian Daub, and The Virus in the Age of Madness (2020) by Bernard-Henri Lévy—each explore how rapid technological, ideological, and biological forces disrupt societal structures. However, their critiques and solutions diverge in scope and focus. Each grapples with the tension between progress and human agency, but through distinct lenses. Azhar emphasizes institutional lag in the face of exponential technology, Daub deconstructs Silicon Valley’s self- mythologizing, and Lévy warns against medical authoritarianism and societal division during crises. Each work intersects with Friedman’s socioeconomic and geopolitical philosophies surrounding technocratic oversight.
Power Dynamics and Institutional Failure
Azhar and Lévy highlight how concentrated power, whether in tech giants or medical authorities, manipulate systemic gaps. Azhar’s exponential gap theory argues that institutions fail to regulate tech-driven economic shifts. Which enables monopolies, erosion of labor rights, and hinders democratic oversight. Similarly, Lévy critiques the medical gaze surrounding COVID19. This involves unchallenged public health mandates and authoritarian overreach. Daub complements this by exposing how the technology industry’s narrative of inevitability masks corporate regulatory evasion as revolutionary progress. All three authors concur that unchecked power flourishes when society lacks frameworks to balance rapid change with ethical liability.
Mythmaking vs. Reality
Daub and Azhar explore narratives used to justify disruption. Daub traces technology’s reliance on recycled philosophies (i.e., Ayn Rand’s individualism, Marshall McLuhan’s medium- centralism) to describe exploitation, such as gig work framed as self-expression. Meanwhile, Azhar shows how technology firms promote marketing hype based on exaggerations, e.g., Gartner’s AI Hype Cycle. Each author reveals disconnects between technology’s perception and its impacts on society. Lévy extends this critique with examples about the COVID-19 pandemic. He rejects romanticization of government-mandated lockdowns. He also condemns the divide between privileged decision makers and those suffering economic or isolationist harm.
Human Agency in Crisis
While Azhar and Lévy advocate proactive solutions to systemic risks, their approaches differ. Azhar calls for collective action to bridge the exponential gap through a digital bill of rights, reformation of antitrust, and green-cautious technology investments. However, Lévy prioritizes philosophical resistance. This entails a revival of democratic engagement, rejection of survivalist paranoia, and reassertion of ethical obligations. Daub is skeptical of technology’s capacity for self-correction. Thus, he urges society to contend with industry’s selective amnesia. But, instead, to learn from mistakes of the past. All three books underscore the need to replace passive acceptance of disruption with deliberate oversight.
Divergent Scopes of Critique
Azhar’s work is macroeconomic and geopolitical, analyzing how computing, energy, biology, and manufacturing are reshaping society. Daub’s focus is cultural, dissecting technology’s intellectual pretensions and their social costs. Lévy’s critique is existential, associating pandemic responses to a broader erosion of humanistic values. Yet he overlaps Daub’s analysis of technology’s mimetic desire and mirrors Azhar’s warnings about splinternet fragmentation. While Lévy’s warnings about isolationism resonate with Azhar’s observations on declining global cooperation. Together, they describe the world’s struggles in reconciling progress. Each author agrees that solutions require ingenuity and a reaffirmation of humanity.
Public Reception of Works
The Exponential Age
When released, Azeem Azhar’s The Exponential Age was met with commendation for its well-reasoned analysis, relevance, and constructive outlook (Smith P. , 2021). Azhar’s book is considered a significant contribution to the public discourse on technology’s role in shaping the future. It offers a roadmap to navigate exponential change. His work is accessible and relevant to a broad audience (Turck, 2022). Reviewers highlight his ability to synthesize multiple disciplines (e.g., physics, economics, political science) (Rotman, 2021).
What Tech Calls Thinking
Adrian Daub’s What Tech Calls Thinking was well-received as a rigorous critique of Silicon Valley’s ideological base. Critics value the book for its historical and philosophical insights. Daub recommends the book to readers seeking to understand the myths and ideas shaping culture and technology (Adams, 2020). Though, it received criticism for its academic perspective (Seidl, 2020), and being too broad with fundamental concepts (Lundblad, 2021).
The Virus in the Age of Madness
While Bernard-Henri Lévy’s earlier works were often criticized for factual inaccuracies, misuse of sources, and grammatical mistakes, Virus in the Age of Madness has received approval from critics and appeal from readers (Smith B. , 2021). Some reviewers focus on the book’s argumentative style, rhetoric, contradictions, and philosophical questions (Kirkus Reviews, 2020). In retrospect, Lévy’s criticisms are exacerbated with the Trump White House’s recent claims the virus’s origins (WhiteHouse.gov, 2025). Moreso, with recent claims about the Biden administration’s efforts to suppress evidence about the pandemic’s origins and engage in a campaign of “delay, confusion, and non-responsiveness” (Rubin, 2025) (para. 5).
Friedman Intersections
Azhar
Azhar’s work on the exponential pace of technological change and the institutional lag thereof relates to Friedman’s insights on socioeconomics and the challenges that emerged in the US post WWII with a technocratic governance absorbed with theory instead of pragmatism. Both highlight the need for adaptive, accountable institutions capable of managing rapid change to prevent social and political crises. Moreso, Azhar’s exponential gap reflects the widening divide Friedman describes in his institutional and industrial cycles.
Daub
Daub’s work relates to Friedman’s by critically examining the ideological and institutional forces that shape contemporary technological and political power. Both highlight the risks posed by technocratic and neoliberal elites who promote narratives of inevitability that obscure democratic deficits. Moreso, by promoting individualism that masks social inequalities. Their combined insights deepen understanding of how cultural mythology and institutional dynamics interact to influence governance and societal outcomes in the age of rapid technological change.
Lévy
Lévy’s work relates to Friedman’s by providing a philosophical and political critique of institutional overreach and the resulting democratic crises during the pandemic. Both call for renewed representative oversight and ethical vigilance to counterbalance the dominance of shortsighted expert authority in times of societal upheaval. Lévy emphasizes the danger of infallible scientific consensus, which stifles debate and accountability. Friedman similarly notes that reliance on expert authority without checks and balances generates political divide.
Key Takeaways
The Exponential Age by Azeem Azhar, What Tech Calls Thinking by Adrian Daub, and The Virus in the Age of Madness by Bernard-Henri Lévy each examine the impact of rapid change on society—whether technological, ideological, or biological. Despite their differing subjects, all three books converge to circumvent disruptive forces at play against society through ethical vigilance and collective action.
Rapid Change Outpaces Institutions
Azhar’s The Exponential Age highlights the widening divide between technological innovation and society’s ability to adapt its laws, institutions, and cultural norms. However, there is a lag in this adaptation (i.e., the exponential gap) which results in rising inequality, unchecked corporate power, and systemic vulnerabilities. The gap can be seen in the gig economy, data privacy, and pandemic responses. Azhar calls for collective action and new frameworks to ensure that the benefits of exponential technologies are broadly shared. Moreso, to ensure that these technologies do not entrench the power of large technology corporations.
Tech Mythology and Accountability
Daub’s What Tech Calls Thinking dissects how the technology industry constructs selfserving myths. In other words, repacking old ideas as revolutionary, promoting narratives of inevitable progress, and glorifying individualism. This mythology obscures historical context, limits accountability, and perpetuates privilege (or lack thereof). This is articulated in the gig economy and college dropout examples. Finally, Daub warns that technology’s selective amnesia and platform primacy enable exploitation, devalue labor, and allow companies to evade responsibility for societal harms.
Authority, Freedom, and Human Values in Crisis
Lévy’s The Virus in the Age of Madness critiques the elevation of medical authority and the reduction of life to biological survival during the COVID-19 pandemic. He warns that unchecked medical and technological power can erode democratic debate, civil liberties, and ethical engagement. Lévy rejects the romanticization of lockdowns, instead calling for pragmatic, humane reactions. He calls for responses that prioritize social bonds, intellectual life, and global responsibility to the vulnerable.
Shared Themes and Contrasts
All three books caution against the dangers of unchecked power within technology corporations, medical authorities, or platform owners. They also express warning against the erosion of democratic oversight and ethical responsibility. Each author emphasizes the importance of historical awareness and critical thinking. Moreso, they highlight the need to resist narratives that frame disruption as inevitable or virtuous.
While Azhar is optimistic about the potential for society to shape technological outcomes through policy and collective action, Daub is more skeptical of the technology industry’s willingness to correct itself. Lévy is concerned about the loss of humanistic values in the face of crisis. However, the books collectively argue for the reclamation of agency to ensure that progress serves the betterment of society. The authors call upon individuals, communities, and institutions to impose moral foundations. Rather than reinforcing privilege, isolation, or authoritarian control.
Concluding Thoughts
In summary, the analysis and contrast between The Exponential Age, What Tech Calls Thinking, and The Virus in the Age of Madness reveal three distinct but connected critiques of how modern society responds to rapid change. All three books criticize the consequences of rapid technological, ideological, and biological change. Moreso, each book intersects philosophies of Dr. Geroge Friedman. Azhar analyzes institutional lag and economic disruption—paralleling Friedman’s American institutional and industrial cycles. Daub dissects the cultural narratives and myths of the technology industry—paralleling Friedman’s geopolitical and institutional analysis of technocracy and neoliberalism. Lévy warns of the philosophical and ethical dangers of crisis-driven authority—paralleling Friedman’s political critique of technocratic overreach. While each book differs in scope, they emphasize the need for criticism, vigilance, and unity. And together, they seek to ensure progress serves humanity rather than entrenching power and inequality.
Appendices
Appendix A
Bibliography
Abraham, K. G., Haltiwanger, J., Hou, C., Sandusky, L. K., & Spletzer, J. (2025). Driving the Gig Economy. NBER Working Paper No. w32766, 1-48. Retrieved from https://ssrn.com/abstract=4915953
Adams, J. (2020). What Tech Calls Thinking: Book Review. Retrieved from medium.com: https://journojoshua.medium.com/what-tech-calls-thinking-book-review-91ca4fb248e8
Arcuri, L. (2019). 4 Contributing Factors to Declining Fertility Rates: A Global Overview. Retrieved from GE HealthCare
Voluson Club: https://www.volusonclub.net/empowered-womens-health/4-contributing-factors-to-declining-fertilityrates-a-global-overview/
Arshad, R. (2023). Improving Cloud Security with DevSecOps: Best Practices for Azure. Retrieved from medium.com: https://medium.com/@arshriz/best-practices-for-implementing-cloud-native-devsecops-in-azure-13a9062cee92
Atkins, C. G., & Das, S. (2022). What Should Clinicians and Patients Know About the Clinical Gaze, Disability, and Iatrogenic Harm When Making Decisions? AMA Journal of Ethics.
Azhar, A. (2021). The Exponential Age. Diversion Books.
Azhar, A. (2021). The Exponential Age Will Transform Economics Forever. Retrieved from wired.com: https://www.wired.com/story/exponential-age-azeem-azhar/
Barbarino, M. (2022). What is Nuclear Fusion. Retrieved from iaea.org: https://www.iaea.org/newscenter/news/what-is-nuclearfusion
Blease, C. (2023). Groupthink is stifling the university. Retrieved from spiked-online.com: https://www.spikedonline.com/2023/04/26/groupthink-is-stifling-the-university/
Blokdyk, G. (2021). FedRAMP: A Complete Guide. 5STARCooks.
BLS. (2022). The Impact of COVID-19 on Labor Markets and Inequality. Bureau of Labor Statistics Working Paper 551, 1-37. Retrieved from https://www.bls.gov/osmr/research-papers/2022/pdf/ec220060.pdf
Browne, R. (2024). Why Big Tech is turning to nuclear to power its energy-intensive AI ambitions. Retrieved from cnbc.com: https://www.cnbc.com/2024/10/15/big-tech-turns-to-nuclear-energy-to-fuel-power-intensive-ai-ambitions.html
Buckles, E., Jones, D., Paulhus, D. L., a, b, c, . . . e. (2013). Behavioral Confirmation of Everyday. APS 24-11, 2201–2209.
Byrd, J. (2024). 9 Signs It’s Time to Upgrade Your ERP. Retrieved from mdm.com: https://www.mdm.com/article/featured/featured-main/9-signs-its-time-to-upgrade-your-erp/
Calma, J. (2023). Microsoft is going nuclear to power its AI ambitions. Retrieved from theverge.com: https://www.theverge.com/2023/9/26/23889956/microsoft-next-generation-nuclear-energy-smr-job-hiring
Canboy, B., & Khlif, W. (2025). Beyond efficiency: Revisiting AI platforms, servitization and power relations from a critical perspective. International Journal of Production Economics, 109550.
Chao, B. (2024). SAP Introduces Financial Incentives to Encourage Hong Kong Companies to Move to the Cloud. Retrieved from news.sap.com/: https://news.sap.com/hk/2024/02/sap-introduces-financial-incentives-to-encourage-hong-kongcompanies-to-move-to-the-cloud
Chaudhary, A. (2023). Managing Cloud Misconfigurations Risks. Retrieved from cloudsecurityalliance.org: https://cloudsecurityalliance.org/blog/2023/08/14/managing-cloud-misconfigurations-risks
Chen, T.-C. T., & Lin, Y.-C. (2019). A three-dimensional-printing-based agile and ubiquitous additive manufacturing system. Robotics and Computer-Integrated Manufacturing, 88-95. Retrieved from https://www.sciencedirect.com/science/article/abs/pii/S0736584517302594
Chu, E., & Tarazano, D. L. (2025). A Brief History of Solar Panels. Retrieved from Smithsonian Magazine: https://www.smithsonianmag.com/sponsored/brief-history-solar-panels-180972006/
Cisco. (2025). 2025 Annual Report. Retrieved from cisco.com: https://www.cisco.com/c/en/us/products/security/state-of-aisecurity.html
Cole, J. (2020). Marshall McLuhan and Cultural Studies. Retrieved from winnsox.com: https://winnsox.com/journal/article/marshall-mcluhan-and-cultural-studies
Congress, 1. (2022). H.R.7535 - Quantum Computing Cybersecurity Preparedness Act. Washington DC: 117th Congress.
Coshow, T. (2024). Build AI Agent Services to Revolutionize Client Operations. Gartner. Retrieved from https://www.nice.com/lps/rpcs-gartner-ai-agents?utm_campaign=NL_Q125_EN_PLT_GLOB_243695_CLP_RPCSGartner-Build-AI-Agent&utm_source=google&utm_medium=cpc&utm_content=0295424&utm_detail=dentsu-allus_ca-gartner&gad_source=1&gbraid=0AAAAACq5q8EEDdxtZgrEnq-kC
Daub, A. (2020). What Tech Calls Thinking: An Inquiry into the Intellectual Bedrock. FSG Originals.
Davis, D. (2019). Why We Must Reckon With The Tech Hype Gap. Retrieved from Forbes Communications Council: https://www.forbes.com/councils/forbescommunicationscouncil/2019/07/05/why-we-must-reckon-with-the-tech-hypegap/
Deloitte. (2021). Maximizing the impact of technology investments in the new normal. Retrieved from CIO Insider: https://www2.deloitte.com/us/en/insights/focus/cio-insider-business-insights/impact-covid-19-technology-investmentsbudgets-spending.html
Dikicioglu, D., & Borgosz, L. (2024). Internet of Things: A New Era for Biomanufacturing. Retrieved from thechemicalengineer.com: https://www.thechemicalengineer.com/features/internet-of-things-a-new-era-forbiomanufacturing/
DOE. (2025). Breaking It Down: Next-Generation Batteries. Retrieved from Energy.gov: https://www.energy.gov/eere/ammto/breaking-it-down-next-generation-batteries
Dolan, E. W. (2023). YouTube’s recommendation system exhibits left-leaning bias, new study suggests. Retrieved from psypost.org: https://www.psypost.org/youtubes-recommendation-system-exhibits-left-leaning-bias-new-study-suggests
Doyle, C., Carlos, J., & Serrato, S. (2024). Best-laid plans: How multinationals minimize taxes. Retrieved from stanford.edu/publications: https://siepr.stanford.edu/publications/policy-brief/best-laid-plans-how-multinationalsminimize-taxes
EIA. (2023). STEO Between the Lines: Small-scale solar accounts for about one-third of U.S. solar power capacity. Retrieved from eia.gov: https://www.eia.gov/outlooks/steo/report/BTL/2023/09-smallscalesolar/article.php
Euchner, J. (2021). Marshall McLuhan and the Next Normal. Research-Technology Management , 9-10.
Faber, S., Williams, M. T., & Skinta, M. (2024). Power, discrimination, and privilege in individuals and institutions. Frontiers in Sociology.
FedSoc. (2023). Are Digital Bills of Rights A Sound Solution to Conflict Among Tech Companies, Consumers, and Government? Retrieved from fedsoc.org/commentary: https://fedsoc.org/commentary/fedsoc-blog/are-digital-bills-of-rights-a-soundsolution-to-conflict-among-tech-companies-consumers-and-government
Fenn, J., & Linden, A. (2003). Understanding Gartner's Hype Cycles. Gartner Reserach.
Fenn, J., & Raskino, M. (2008). Mastering the Hype Cycle: How to Choose the Right Innovation at the Right Time. Harvard Business Review Press.
Fernando, J. W., Burden, N., Judge, M., O’Brien, L. V., Ashman, H., Paladino, A., & Kashima, Y. (2022). Profiles of an Ideal
Society: The Utopian Visions of Ordinary People. Journal of Cross-Cultural Psychology Volume 54, Issue 1, 43-60.
Foucault, M. (1994). The Birth of the Clinic: An Archaeology of Medical Perception. Vintage.
Friedman, G. (2020). The Storm Before the Calm. Doubleday.
Friedman, G. (2021). The 2020s and the Rebuilding of America. (C. C. podcast, Interviewer)
Friedman, T. (2005). The World is Flat. Farrar, Straus and Giroux.
Gardels, N. (2021). The Last Humanist. Retrieved from Noema Magazine: https://bernard-henri-levy.com/en/the-last-humanist/
Gartner. (2019). Gartner Hype Cycle for Artificial Intelligence. Retrieved from gartner.com: gartner.com/smarterwithgartner
Gartner. (2025). Cybersecurity and AI: Enabling Security While Managing Risk. Retrieved from gartner.com: https://www.gartner.com/en/cybersecurity/topics/cybersecurity-and-ai
Green, D. (2025). René Girard's Mimetic Theory in Business or Why Peter Thiel Loves this Guy. Retrieved from linkedin.com/pulse: https://www.linkedin.com/pulse/ren%C3%A9-girards-mimetic-theory-business-why-peter-thielloves-green-ujryc/
Guzzo, K. (2025). NPR Fresh Air - What's behind the 'pronatalist' movement to boost the birth rate? (T. Mosley, Interviewer)
Hanna, C. (2023). Making sense of SAP RISE: 4 key considerations. Retrieved from cio.com: https://www.cio.com/article/480408/making-sense-of-sap-rise-4-key-considerations.html
Holzer, H. J. (2022). Understanding the impact of automation on workers, jobs, and wages. Retrieved from brookings.edu/articles: https://www.brookings.edu/articles/understanding-the-impact-of-automation-on-workers-jobsand-wages/
Horn, M. B. (2020). A gap year shouldn’t be just for the privileged, especially now. Retrieved from ChristensenInstitute.org/Blog: https://www.christenseninstitute.org/blog/a-gap-year-shouldnt-be-just-for-the-privileged-especially-now/
Humble, K. (2024). War, Artificial Intelligence, and the Future of Conflict. Retrieved from GeorgeTown.edu: https://gjia.georgetown.edu/2024/07/12/war-artificial-intelligence-and-the-future-of-conflict/
Huminski, J. (2020). The Virus in the Age of Madness. Retrieved from Diplomatic Courier: https://www.diplomaticourier.com/posts/the-virus-in-the-age-of-madness
Hwang, T.-J., Rabheru, K., Peisah, C., Reichman, W., & Ikeda, M. (2020). Loneliness and social isolation during the COVID-19 pandemic. Int Psychogeriatr 32(10), 1217-1220.
IBM. (2025). Artificial intelligence (AI) cybersecurity. Retrieved from ibm.com: https://www.ibm.com/ai-cybersecurity
Ibrahim, H., AlDahoul, N., Lee , S., Rahwan, T., Zaki, Y., & al, e. (2023). YouTube’s recommendation algorithm is left-leaning in the United States. PNAS Nexus, 264. Retrieved from https://pmc.ncbi.nlm.nih.gov/articles/PMC10433241/
Iyer, P. (2023). New Study Suggests Right-Wing Bias in YouTube Recommendation Algorithm. Retrieved from techpolicy.press: https://www.techpolicy.press/new-study-suggests-rightwing-bias-in-youtube-recommendation-algorithm/
Johnson, R. C. (2013). Moore’s Law trumped by Wright’s Law. Retrieved from EE Times: https://www.eetimes.com/moores-lawtrumped-by-wrights-law/
Kashima, Y., & Fernando, J. (2020). Utopia and ideology in cultural dynamics. Current Opinion in Behavioral Sciences, Volume 34, 102-106.
Kearney, M. S., & Levine, P. (2023). US births are down again, after the COVID baby bust and rebound. Retrieved from brookings.edu: https://www.brookings.edu/articles/us-births-are-down-again-after-the-covid-baby-bust-and-rebound/
King, B. (2022). What's New In Additive Manufacturing. Retrieved from Forbes Tech Council: https://www.forbes.com/councils/forbestechcouncil/2022/05/20/whats-new-in-additive-manufacturing/
Kirkus Reviews. (2020). kirkusreviews.com - THE VIRUS IN THE AGE OF MADNESS. Retrieved from kirkusreviews.com: https://www.kirkusreviews.com/book-reviews/bernard-henri-levy/the-virus-in-the-age-of-madness/
Klein v. Facebook Inc., 20-CV-08570-LHK (United States District Court, N.D. California 2022).
Kottász, Z. (2023). We are entering a period of warfare: An Interview with George Friedman. Retrieved from europeanconservative.com: https://europeanconservative.com/articles/interviews/we-are-entering-a-period-of-warfarean-interview-with-george-friedman/
Lacey, N., Jackson, C., & Feldman, S. (2021). Covid-19 one year on: Global public loses confidence in institutions. Retrieved from ipsos.com: https://www.ipsos.com/en/covid-19-one-year-global-public-loses-confidence-institutions
Lam, K. (2024). Privacy Mismanagement: Privacy Harms, Digital Market. Hastings Law Journal 75, 1795-1822.
Lévy, B.-H. (2020). The Virus in the Age of Madness. Yale University.
Lévy, P. (2011). The Semantic Sphere 1: Computation, Cognition and Information Economy. Wiley-ISTE.
Li, T. C. (2021). How Facebook, Amazon and Google abused the Patriot Act after 9/11. Retrieved from msnbc.com/opinion: https://www.msnbc.com/opinion/how-facebook-amazon-google-abused-patriot-act-after-9-11-n1278964
Lin, L. y., Sidani, J. E., Shensa, A., Radovic, A., Miller, E., Colditz, J. B., . . . Primack, B. A. (2016 ). Association between Social Media Use and Depression among U.S. Young Adults. Depress Anxiety, 323–331.
Lundblad, N. B. (2021). A note on “What Tech Calls Thinking” by Adrian Daub. Retrieved from unpredictablepatterns.com: https://unpredictablepatterns.com/2021/03/08/a-note-on-what-tech-calls-thinking-by-adrian-daub/
Maurer, R. (2010). Beyond the Wall of Resistance. Bard Press.
McCormick, D. (2012). Wright's Law Edges Out Moore's Law in Predicting Technology Development. Retrieved from IEEE Spectrum: https://spectrum.ieee.org/wrights-law-edges-out-moores-law-in-predicting-technology-development
McLemee, S. (2020). Scott McLemee reviews Bernard-Henri Lévy's The Virus in the Age of Madness. Retrieved from Inside
Higher Ed: https://www.insidehighered.com/views/2020/08/21/review-bernard-henri-l%C3%A9vy-virus-age-madness
McLuhan, M. (1964). Understanding Media: The Extensions of Man. The MIT Press.
McLuhan, M., & Fiore, Q. (2001). The Medium is the Massage. Gingko Press.
Miller, C. (2025). Does Social Media Use Cause Depression? Retrieved from Child Mind Institute: https://childmind.org/article/is-social-media-use-causing-depression/
NIST. (2022). NCCoE DevSecOps Workshop. NIST NCCoE. Retrieved from https://www.nccoe.nist.gov/get-involved/attendevents/nccoe-devsecops-workshop
Ogburn, W. (1922). Social Change with Respect to Culture and Original Nature.
Ollman, B. (2005). The Utopian Vision of the Future (Then and Now): A Marxist Critique. Retrieved from monthlyreview.org: https://monthlyreview.org/2005/07/01/the-utopian-vision-of-the-future-then-and-now-a-marxist-critique/
Panetta, K. (2019). Is the Cloud Secure. Retrieved from gartner.com: https://www.gartner.com/smarterwithgartner/is-the-cloudsecure
Pattat, E. (2023). Did the USA Patriot Act Cause Democratic Backsliding in the US? Retrieved from democratic-erosion.org: https://democratic-erosion.org/2023/11/21/did-the-usa-patriot-act-cause-democratic-backsliding-in-the-us/
Paulhus, D. L., & Williams, K. M. (n.d.). Dark Triad. 2002: Psychology Today United Kingdom.
Peikoff, L. (1993). Objectivism: The Philosophy of Ayn Rand. Meridian.
Piscione, D. P. (2013). Secrets of Silicon Valley: What Everyone Else Can Learn from the Innovation Capital of the World. St. Martin's Press.
Rathore, A. S., Nikita, S., & Jesubalan, N. G. (2022). Digitization in bioprocessing: The role of soft sensors in monitoring and control of downstream processing for production of biotherapeutic products. Biosensors and Bioelectronics: X, 100-263.
Reform, C. o. (2023). White House Policy on AI. Washington DC: Cybersecurity, Information Technology, and Government
Innovation. Retrieved from https://oversight.house.gov/release/hearing-wrap-up-u-s-must-not-stifle-ai-innovation-inestablishing-guardrails-for-use
Reuters. (2025). China's CATL launches new sodium-ion battery brand. Retrieved from Reuters: https://www.reuters.com/technology/chinese-battery-maker-catl-launches-second-generation-fast-charging-battery2025-04-21/
Rockwell Automation. (2025). State of Smart Manufacturing Report. Rockwell Automation.
Rotman, D. (2021). Book Review Azeem Azhar. Retrieved from technologyreview.com: https://www.technologyreview.com/2021/10/27/1037169/book-review-azeem-azhar/
Rozenshtein, A. Z. (2023). Interpreting the ambiguities of Section 230. Retrieved from brookings.edu: https://www.brookings.edu/articles/interpreting-the-ambiguities-of-section-230/
Rubin, A. (2025). White House pushes COVID lab leak theory with new website. Retrieved from axios.com: https://www.axios.com/2025/04/18/covid-lab-leak-website-trump-white-house
Sacks, D. O., & Thiel, P. (1998). The Diversity Myth : Multiculturalism and Political Intolerance on Campus. Independent Institute.
Sankararaman, G. (2024). Gig Economy's Impact On Workforce Dynamics And Economic Resilience. Educational Administration Theory 30(6), 1627-1634.
Sanzeri, S. (2023). What The Quantum Computing Cybersecurity Preparedness Act Means For National Security. Retrieved from Forbes: https://www.forbes.com/councils/forbestechcouncil/2023/01/25/what-the-quantum-computing-cybersecuritypreparedness-act-means-for-national-security/
Schneider, T. W. (2019). Taxi, Uber, and Lyft Usage in New York City. Retrieved from toddwschneider.com: https://toddwschneider.com/posts/taxi-uber-lyft-usage-new-york-city/
Schramm, M. A. (2025). CURB YOUR ENTHUSIASM: WHY EUROPE’S DIGITAL REFORMS MAY NOT BECOME A GLOBAL STANDARD. LT Special Issue, 61-100.
Seidl, T. (2020). Thinking, Shallow but Powerful Book Review: Adrian Daub, What Tech Calls Thinking. Retrieved from timoseidl.com: https://www.timoseidl.com/blog/what-tech-calls-thinking
Smith, B. (2021). It’s Time to Take Bernard-Henri Lévy Seriously. Retrieved from foreignpolicy.com: https://foreignpolicy.com/2021/04/09/bernard-henri-levy-bhl-france-philosophy-public-intellectual/
Smith, P. (2021). Exponential by Azeem Azhar review – bridging the technology gap. Retrieved from theguardian.com: https://www.theguardian.com/books/2021/sep/15/exponential-by-azeem-azhar-review-bridging-the-technology-gap
Trotter, G. (2023). COVID-19 and the Authority of Science. HEC Forum, 111-138.
Turck, M. (2022). In Conversation with Azeem Azhar, Author, The Exponential Age. Retrieved from mattturck.com: https://mattturck.com/azhar/
Volkmer, S. A., Gaube, S., Raue, M., & Lermer, E. (2023). Troll story: The dark tetrad and online trolling revisited with a glance at humor. PLoS One.
Wang, Y., Zhao, Y., Bollas, A., Wang, Y., Au, K. F., & aaa, b. (2021). Nanopore sequencing technology, bioinformatics and applications. Nature Biotechnology 39, 1348–1365.
Wellspring. (2024). Top 5 Synthetic Biology Innovations and Laatest Technologies. Retrieved from Wellspring Blog: https://www.wellspring.com/blog/top-5-synthetic-biology-innovations-and-latest-technologies
WhiteHouse.gov. (2025, 5 4). The True Origins of COVID-19. Retrieved from WhiteHouse.gov: https://www.whitehouse.gov/lab-leak-true-origins-of-covid-19/
Winton, B. (2019). Moore’s Law Isn’t Dead: It’s Wrong - Long Live Wright’s Law. Retrieved from ark-invest.com: https://www.ark-invest.com/articles/analyst-research/wrights-law-2
WNA. (2021). Advanced Nuclear Power Reactors. Retrieved from world-nuclear.org: https://world-nuclear.org/informationlibrary/nuclear-fuel-cycle/nuclear-power-reactors/advanced-nuclear-power-reactors
Wodajo, E. (2025). Resurgence of ''common sense'' policy and Trade. Retrieved from The Engagement Edge: https://www.linkedin.com/pulse/rise-common-sense-policy-trade-ermias-wodajo-4m48f/
Wooldridge, A. (2023). America's Educational Superpower is Fading. Retrieved from Bloomberg: https://www.bloomberg.com/opinion/articles/2023-04-18/higher-education-in-the-us-faces-a-systemic-crisis
Wright, T. P. (1936). Factors Affecting the Costs of Airplanes.
Zhang, W., & Banerji, S. (2017). Challenges of servitization: A systematic literature review. Industrial Marketing Management Volume 65, 217-227.
Zhu, Y., Zhang, L., Zhou, X., Li, C., & Yang, D. (2021). The impact of social distancing during COVID-19: A conditional process model of negative emotions, alienation, affective disorders, and post-traumatic stress disorder. J Affect Disord, 131-137.
Spam Nation Book Review
James V. Tarlton
3/5/2025
Abstract
Spam Nation by cybersecurity expert Brian Krebs, a New York Times bestseller, exposes the global crime rings behind spam, hacking, and online pharmacy scams that steal Americans’ data, money, and even endanger lives. Using investigative reporting and insider interviews, Krebs reveals how cybercriminals infiltrate our everyday lives, the billions lost to fraud, and offers practical ways to protect ourselves from this growing threat.

Introduction
Brian Krebs’s New York Times bestseller, Spam Nation, is a gripping exposé of the sprawling, dangerous world of global cybercrime. He focuses on the networks and individuals behind spam, hacking, and online pharmacy scams. Through methodical investigative reporting, Krebs traces the rise, fall, and resurgence of what he calls the “digital mafia”—the underground networks responsible for email spam, malware, phishing, spyware, and especially rogue online pharmacies targeting Americans. His investigation delves into how these operations function, profiling the masterminds who run them and revealing the vast profits they make by stealing from unsuspecting people.
Insider Perspectives
Krebs’s narrative is strengthened by insider perspectives, thanks to his firsthand interviews and direct interactions with cybercriminals—sometimes traveling abroad and meeting figures like “Cosma” in person. He documents their rivalries, betrayals, and power struggles, offering a rare look into both the personalities fueling global spam and the technical infrastructure behind their schemes. Importantly, Krebs highlights the everyday impact of these crimes on Americans, exploring how individuals—sometimes out of desperation over high drug prices or embarrassment—become entangled in illicit online pharmacies. This puts not only their finances at risk but also their health, as unregulated and potentially dangerous medications are often peddled through these illegal channels. Even those who avoid opening suspicious emails can find themselves targeted, as spammers exploit vulnerabilities to gain entry into personal and business accounts using advanced hacking and phishing tactics.
White-Hat Hackers
The financial and safety toll substantiated in Spam Nation is staggering, with billions of dollars lost to fraud and genuine threats posed by toxic or ineffective drugs. Krebs demonstrates that cybercrime is not just a nuisance—it can endanger lives. His work combines deep technical research with persistent reporting. Krebs forges relationships not only with cybersecurity experts and white-hat hackers but also with cybercriminals themselves. His willingness to take personal risks results in exclusive stories and rare insights, often outpacing law enforcement efforts. He also scrutinizes how American companies respond to these threats, critiquing weak anti-spam and anti-phishing efforts and revealing how spammers sometimes manipulate or co-opt supposed safeguards.
Considerations
For readers concerned about their own safety, Krebs concludes Spam Nation with clear, practical advice. He urges people not to install unsolicited software, to remain wary of emails by not clicking links or opening attachments from unknown or unexpected senders, and to use strong, unique passwords—enabling multi-factor authentication whenever possible. Krebs emphasizes that everyone, regardless of their technical background, plays a role in safeguarding their digital life. He encourages personal vigilance, skepticism toward unsolicited offers, careful monitoring of finances, and the pursuit of legitimate sources for online purchases—especially when it comes to medication. While Krebs paints a vivid picture of the enormity and complexity of global cybercrime, he also offers hope, noting positive trends such as skilled talent moving into legitimate cybersecurity roles and the increasing effectiveness of defensive technologies. Spam Nation is ultimately both a true-crime thriller and an indispensable handbook for digital self-defense, reinforcing that informed vigilance is our best weapon against the ongoing threat of cybercrime.
In Closing
Ultimately, Brian Krebs’s Spam Nation investigates the criminal networks running global spam, hacking, and fake online pharmacies. Through firsthand reporting and interviews with insiders, Krebs reveals how these cybercriminals steal money, data, and even endanger lives by selling unsafe drugs. He describes the vast financial losses and personal risks ordinary Americans face, then offers practical advice for self-protection: be cautious with emails, use strong and unique passwords, and avoid suspicious online offers. Ultimately, the book is both a true-crime story and a guide to defending against digital threats.
Bibliography
Krebs, B. (2014). Spam Nation: The Inside Story of Organized Cybercrime - from Global Epidemic to Your Front Door. Naperville, Illinois: Sourcebooks.
Technology and Society Book Review
James V. Tarlton
1/13/2025
Abstract
Johnson and Wetmore's Technology and Society explains how tech change is shaped by societal values as much as by practical concerns. To guide technology for the better, we must recognize how technology and society are deeply connected. The book covers visions of the future, core theories in Science and Technology Studies (STS), the role of human values in tech choices, and how issues like race and gender intersect with technology. It concludes with readings on current sociotechnical challenges, including cybersecurity, geoengineering, and the myth of technology’s neutrality.

Introduction
Johnson and Wetmore’s Technology and Society presents a central argument: technological change is shaped just as much by societal values as by practical, technical, or economic considerations. The book emphasizes that technological development never happens in isolation—decisions about which technologies to promote, design, or adopt are tightly linked to questions about whose values matter, what gets prioritized, and how social forces (from culture to regulation) drive or restrain innovation.
To guide technology for the better, Johnson and Wetmore stress that society must not treat technology as something separate or inevitable. Instead, they showcase how deeply interwoven technology and society are: people’s beliefs, values, and visions for the future shape technologies, just as technologies, in turn, reshape societies. Their curated selections invite readers to see themselves as active participants—both shaping and being shaped by technological systems—and to understand that influencing the direction of technology depends on critically reflecting on values, politics, and social dynamics as much as on technical feasibility.
Books Dimensions
Visions of the Future: It begins with essays and readings that depict both hopeful utopias and cautionary tales about technology’s possible trajectories. These visions are contrasted to highlight that how we imagine technology’s future guides real-world decisions about which paths to pursue or avoid.
Core Science and Technology Studies (STS) Theories: Johnson and Wetmore introduce key concepts from STS, such as social constructivism (the idea that society co-creates technology), actor-network theory (which treats humans and non-humans as interconnected actors), and path dependence (how early choices lock in future directions). These frameworks challenge the notion of technological determinism and show that choices and values matter at every stage.
Human Values in Technological Choices: The book underscores practical examples of how social and human values are embedded in technological design, use, and regulation. For instance, what counts as “safety,” “efficiency,” or “progress” can vary by culture, community, or context, and these contested definitions shape the nature and impact of technological change.
Race, Gender, and Technology: Addressing a gap in earlier thinking, many readings specifically illustrate the ways that race and gender intersect with technology. The book highlights how biases can be inadvertently (or deliberately) built into new systems, and how technologies often reflect—and reinforce—existing social hierarchies. These discussions clarify that issues like discrimination or inequity can be “coded in” to supposedly neutral tools.
Readings on Contemporary Sociotechnical Challenges: The concluding sections tackle pressing challenges in today’s world: cybersecurity, geoengineering, and especially the myth that technology is neutral. The editors argue—and select texts affirm—that solutions to such problems require more than technical fixes: they demand conscious engagement with social context, public values, and inclusive deliberation.
In Closing
In summary, Johnson and Wetmore’s overall message is made clear. Steering technology toward socially desirable ends is only possible when we recognize—through critical, interdisciplinary inquiry—that society and technology are fundamentally intertwined, and that all technological decisions necessarily involve choices about values, power, and justice.
Bibliography
Johnson, D. G., & Wetmore, J. M. (2021). Technology and Society, second edition: Building Our Sociotechnical Future (Inside Technology). Cambridge, Massachusetts: MIT Press.
IT Skills Needed to Run a Business
James V. Tarlton
11/2/2024
Abstract
Entrepreneur Patrice Bertrand offers an excellent story using IT skills to run a business. The Normandy-born innovator whose passion for science, business, and sustainability fueled a distinguished career. After studying chemistry and business in France and serving as a military officer, Patrice developed expertise in the corporate and IT sectors before moving to the U.S. There, he revitalized Roll-Tech Molding Products, a green manufacturer, leading it to success as owner and CEO through innovation and sustainable practices. Patrice’s enduring legacy rests on environmental stewardship, business mentorship, and a commitment to industry progress. His story offers valuable lessons in resilience, leadership, and continuous learning for aspiring entrepreneurs.
Introduction
 Born and raised in the picturesque region of Normandy, France, Patrice Bertrand always had a passion for science and technology.
This led him to study chemistry at the University of Toulouse. During his undergraduate years, Patrice was known for his
dedication and innovative thinking. He often spent long hours in the lab, experimenting with various chemical compounds
and dreaming of making significant contributions to the field.
Born and raised in the picturesque region of Normandy, France, Patrice Bertrand always had a passion for science and technology.
This led him to study chemistry at the University of Toulouse. During his undergraduate years, Patrice was known for his
dedication and innovative thinking. He often spent long hours in the lab, experimenting with various chemical compounds
and dreaming of making significant contributions to the field.
After completing his chemistry degree, Patrice decided to broaden his horizons by pursuing a business degree at the graduate level. He completed an Institut d’Administration des Entreprises (IPA) degree (equivalent to an MBA) in 1982 at Toulouse University of France. This period was not without its challenges. During this time, France required peacetime military conscription, and Patrice enlisted as an officer in the 35th Regiment d’Artillery Parachutist. The rigorous training and discipline of the military shaped his character, instilling in him a sense of duty, leadership, and perseverance.
Upon completing his military service, Patrice joined the French division of Exxon Chemical Company. For five years, he
honed his skills in the corporate world, learning the intricacies of the chemical industry. Particularly, learning Information
Technology (IT) and setting up information systems, e.g., Enterprise Resource Planning (ERP) software. This is no small task because
learning how to integrate and implement an ERP suited for specific business requires a significant amount of business and technical skills.
From setting up the server and database to configuring the FICO and MRP modules requires
Information Systems skills and Business Process skills.
Equipped with this newly attained knowledge, Patrice yearned for new opportunities to integrate ERP systems. This was a time when the information age was at its inception. In pursuit of his dreams, he moved to the United States, where he spent the next decade working in various manufacturing companies and oversaw information system integrations. His adaptability and technical expertise earned him a reputation as a reliable and innovative professional.
In the early 2000s, Patrice saw an opportunity to make a significant impact. He partnered with Bameco Holdings, LLC, which owned Roll-Tech Molding Products, LLC (RMP), a green manufacturer of wheels and tires made from recycled materials. As the operations manager, Patrice was instrumental in streamlining processes, integrating an ERP, and improving product quality. When Bameco decided to sell Roll-Tech, Patrice seized the opportunity to purchase the company. Despite facing challenges in securing angel investors, he remained undeterred.
 Upon gaining ownership of RMP, Patrice saw the opportunity to overhaul the company's digital prescence. When Bameco sold RMP,
they cloned then split their enterprise-level ERP instance; which, at the time, was SAP ECC 6.0. After the split, this cloned
instance of ECC 6.0 was no longer suiting RMP's needs. Therefore, Patrice, without an IT department at the time, began the journey
of a green-field migration into a new ERP catered for small to medium sized manufacturing companies. The ERP he landed on was
called Global Shop Solutions ERP. Global Shop consists of a large variety of modules. Initially Patrice setup the core
functionality and master data, e.g., accounting, BOM, Routing. Afterward, I had the privilege to join the RMP team to setup
the Planning & Scheduling, BI, CRM, and MRP modules. The ROI of these IT efforts paid off immediately, i.e., 40% reduction
of production lead times, 25% increase in manufacturing performance, and 30% increase in sales.
Upon gaining ownership of RMP, Patrice saw the opportunity to overhaul the company's digital prescence. When Bameco sold RMP,
they cloned then split their enterprise-level ERP instance; which, at the time, was SAP ECC 6.0. After the split, this cloned
instance of ECC 6.0 was no longer suiting RMP's needs. Therefore, Patrice, without an IT department at the time, began the journey
of a green-field migration into a new ERP catered for small to medium sized manufacturing companies. The ERP he landed on was
called Global Shop Solutions ERP. Global Shop consists of a large variety of modules. Initially Patrice setup the core
functionality and master data, e.g., accounting, BOM, Routing. Afterward, I had the privilege to join the RMP team to setup
the Planning & Scheduling, BI, CRM, and MRP modules. The ROI of these IT efforts paid off immediately, i.e., 40% reduction
of production lead times, 25% increase in manufacturing performance, and 30% increase in sales.
 Patrice’s determination paid off when he discovered various government grants and incentives for green manufacturers within the
United States. These opportunities made the ownership of RMP enticing, and he eventually became the President/CEO and owner of
the company. From 2005 to 2019, Patrice led RMP to new heights, increasing sales and expanding the company’s offerings. His
leadership and vision transformed RMP into a successful and respected business. In 2019, Patrice saw another opportunity for
growth and sold RMP to Impact Environmental Group of Illinois.
Patrice’s determination paid off when he discovered various government grants and incentives for green manufacturers within the
United States. These opportunities made the ownership of RMP enticing, and he eventually became the President/CEO and owner of
the company. From 2005 to 2019, Patrice led RMP to new heights, increasing sales and expanding the company’s offerings. His
leadership and vision transformed RMP into a successful and respected business. In 2019, Patrice saw another opportunity for
growth and sold RMP to Impact Environmental Group of Illinois.
After selling RMP, he ventured into consulting for small businesses. With over 30 years of experience, he offers his expertise in manufacturing, general management, and mergers and acquisitions to companies in need. Patrice’s journey is a testament to his resilience, adaptability, and unwavering commitment to excellence. His story continues to inspire aspiring entrepreneurs and business leaders across North America and Western Europe.
Take Aways
Patrice Bertrand, with his extensive experience and successful entrepreneurial journey, offers the following advice to young entrepreneurs:
- Embrace Challenges: Every obstacle is an opportunity to learn and grow. Face challenges head-on and use them as steppingstones to success. Success doesn’t come overnight. Stay committed to your goals, even when the going gets tough. Persistence and determination are key to overcoming setbacks.
- Build Strong Relationships: Networking and building strong relationships with mentors, peers, and industry professionals can provide valuable support and insights. Collaboration often leads to new opportunities.
- Learn ContinuouslyThe business world is dynamic, and continuous learning is essential. Stay updated with industry trends, acquire new skills, and seek knowledge to stay competitive. Patrice’s diverse journey into chemistry, business, and IT exemplifies these principles, and his advice can serve as a valuable guide for aspiring entrepreneurs.
- Environmental Sustainability: Patrice’s dedication to using recycled materials for manufacturing wheels and tires significantly reduced waste and promoted recycling. This not only minimized the company’s environmental footprint but also set a benchmark for other businesses in the industry to follow.
- Innovation and Technology: Patrice’s focus on innovation led to the development of advanced manufacturing techniques, IT best practices, and eco-friendly products. His efforts in research and development not only improved product quality but also positioned RMP as a leader in green manufacturing.
- Support for Small Businesses: After selling RMP, Patrice continued to support the community by offering consulting services to small businesses. His guidance helped many local entrepreneurs navigate challenges, grow their businesses, and adopt sustainable practices.
- Mentorship and Leadership: Patrice’s leadership style emphasized mentorship and personal development. He nurtured a culture of continuous learning and professional growth within RMP, inspiring employees to strive for excellence and innovation.
- Long-Term Vision: Patrice’s strategic vision for RMP ensured the company’s long-term success and sustainability. His forward-thinking approach and commitment to green manufacturing left a legacy of responsible business practices that continue to benefit the community and the environment.
Legacy
Patrice Bertrand’s legacy at Roll-Tech Molding Products, LLC (RMP) is one of environmental stewardship, innovation, and sustainable growth. His commitment to green manufacturing and innovative practices left a lasting impact on both the company and the ecosystem at large. Here are some key aspects of the legacy he left behind:
Conclusion
 Patrice Bertrand’s journey from Normandy to Hickory is a remarkable tale of resilience, innovation, and leadership. His unwavering
commitment to excellence, environmental sustainability, and community engagement has left an indelible mark on the business world
and the communities he served. From his early days as a chemistry student and military officer to his successful tenure as the
President/CEO of Roll-Tech Molding Products, Patrice’s story is one of triumph over adversity and the relentless pursuit of his dreams.
Patrice Bertrand’s journey from Normandy to Hickory is a remarkable tale of resilience, innovation, and leadership. His unwavering
commitment to excellence, environmental sustainability, and community engagement has left an indelible mark on the business world
and the communities he served. From his early days as a chemistry student and military officer to his successful tenure as the
President/CEO of Roll-Tech Molding Products, Patrice’s story is one of triumph over adversity and the relentless pursuit of his dreams.
Patrice Bertrand’s legacy is a testament to the positive impact that a dedicated and visionary leader can have on both a company and its community. His contributions to environmental sustainability, economic growth, and community well-being will be remembered and cherished for years to come.
Through his visionary leadership, Patrice transformed RMP into a beacon of green manufacturing, setting new standards for environmental responsibility and innovation. His legacy extends beyond the company, as he continues to inspire and mentor the next generation of entrepreneurs through his consulting work. Patrice’s story is a testament to the power of perseverance, adaptability, and a deep-rooted commitment to making a positive impact on the world. His journey serves as an inspiration to all who aspire to create meaningful change and leave a legacy.
Political and Legal Environment for International Expansion
James V. Tarlton
10/7/2023
Abstract
When examining the multifaceted decision-making processes that transnational corporations (TNCs) undertake regarding incorporation and operational locations, emphasizing the interplay between home and host country dynamics is paramount. Key factors such as market access, regulatory environments, labor costs, logistics, and political stability are analyzed to illustrate how TNCs strategically select incorporation and operational jurisdictions. The discussion extends to legal mechanisms under international law that mitigate investment risks, including bilateral and multilateral investment treaties, international arbitration frameworks, and political risk insurance, highlighting the practical steps corporations use to safeguard their interests abroad. Furthermore, the paper explores the complex relationship between corporations and state actors, outlining the advantages—such as enhanced market access, regulatory influence, and infrastructure support—and disadvantages, including regulatory scrutiny, exposure to political instability, and reputational risks, inherent in such relationships. The analysis underscores that TNCs must carefully balance these considerations and adopt nuanced strategies to thrive within the evolving global business environment while adhering to relevant legal and ethical standards.
Home and Host country considerations: What factors go into decisions about where to incorporate and where to operate a transnational corporation?
Upon inception of a transnational corporation, home and host country dynamics must be considered. Home-host country factors to consider include components such as market access, regulatory circumstances, labor costs, logistics, and political stability.
Regarding market access, a transnational corporation often considers w here to incorporate and operate based on access to target markets. Incorporation in a country may provide easier access to its domestic market, while operating in a host country can grant access to foreign markets. Legal and regulatory circumstances transnational corporations assess the legal and regulatory framework of both the home and host countries. Favorable regulations, tax incentives, and intellectual property protection can influence their decisions. Labor costs, including wages and benefits, vary between countries. Transnational corporations may incorporate in countries with lower labor costs while targeting markets with higher consumer purchasing power.
Regarding logistics, infrastructure, access to transportation, communication, and supply chain infrastructure is crucial. Transnational corporations often prefer host countries with well-developed infrastructure to streamline operations. Finally, political stability and government policies are essential considerations. Transnational corporations seek countries with stable governments to reduce political risks.
International law and the mitigation of investment risks: What legal instruments and recourses exist that might offset potential legal risks and how would a corporation go about using them?
Regarding the international law and the mitigation of investment risks, legal instruments available to mitigate investment risks include bilateral investment treaties, multilateral investment treaties, international arbitration agreements, and political risk insurance.
Bilateral Investment Treaties (BITs) are a great way to assure a company a smooth transition into international status. These agreements between the two countries aim to protect foreign investments by ensuring fair treatment, dispute resolution mechanisms, and compensation in case of expropriation. Multilateral Investment Treaties are a similar means of reassurance for this transition. Organizations like the World Trade Organization (WTO) and regional groups often offer investment protection agreements that can mitigate risks.
Regarding International Arbitration, transnational corporations can resort to international arbitration mechanisms such as the International Centre for Settlement of Investment Disputes (ICSID) to resolve disputes with host countries. Finally, Political Risk Insurance is a means of mitigation between a company and government which provides additional coverage under certain circumstances. Some governments or international agencies provide this type of insurance to protect a transnational corporation against losses due to political events or conflicts.
Pros and Cons
There are many advantages that can incur from corporate and state relations. These advantages include market access, regulatory influence, and infrastructure support.
Regarding market access, transnational corporations can benefit from favorable trade agreements and diplomatic relations between their home country and host country, facilitating market entry. Regarding regulatory influence, corporations may have a voice in shaping regulations and policies through lobbying efforts and partnerships with governments. Finally, regarding infrastructure support, governments often invest in infrastructure projects that benefit transnational corporations, such as ports or highways.
However, with these advantages come disadvantages between corporate and state relations. Potential disadvantages include regulatory challenges, political instability, and reputation risks.
Regarding regulatory challenges, close ties to governments can lead to regulatory scrutiny and potential conflicts of interest. Regarding political instability, if a transnational corporation is closely aligned with a government, it may face risks when that government experiences political instability. Finally, regarding reputation risks, a transnational corporation can face reputational damage if their relationship with a government is perceived as unethical or exploitative.
In summary, the decisions about where to incorporate and operate, the mitigation of investment risks, and the advantages/disadvantages of a corporation's relationship with governments are complex and multifaceted. Transnational corporations must carefully analyze these factors and develop strategies to navigate the dynamic international business landscape while complying with legal and ethical standards.
TikTok Algorithms Q&A
James V. Tarlton
7/16/2023
Abstract
Earlier this year, I sat down for an interview with Gabriela Tessari from Lenoir-Rhyne University's School of Media to discuss the complex and evolving landscape of AI-driven content moderation on social media platforms. Drawing on my experience as a software engineer specializing in information systems and data science, I answered her questions on topics ranging from TikTok’s censorship algorithms and the rise of "algospeak," to the ethical challenges of balancing user safety with freedom of expression. The conversation explored the technical foundations of algorithmic moderation, its current shortcomings in grasping context and nuance, the risks associated with over-reliance on automated systems, and promising directions for improvement. Presented here is the transcript from that interview, offering insights into the current state and future outlook for AI in content moderation.

How do TikTok’s algorithms currently identify and filter content for censorship? What specific techniques (e.g., keyword filtering, image recognition) are involved in this process?
Algorithms act like expert librarians, organizing and linking users to content that matches their interests. This approach prevents users from being inundated with endless content, allowing them to quickly find what they enjoy. By doing so, algorithms help users discover valuable posts, connect with similar-minded people, and delve deeper into their interests. Also, like librarians, some social media algorithms intend to sway users away from certain content deemed inappropriate. Inappropriate either based on user profile attributes (e.g., age) or based on a higher level, system constraint, e.g., community guidelines. TikTok (2023) claims they use a combination of automated moderation technology and human reviewers to identify and filter content. The algorithms analyze keywords, images, titles, descriptions, and audio to detect violations of community guidelines. Content flagged by the system is then reviewed by human moderators to confirm if it breaches the guidelines.
Could you explain why algospeak works to bypass censorship algorithms? Are there specific weaknesses in content detection that make it easy to bypass?
Algospeak refers to the use of coded expressions, symbols, and euphemisms to evade automated moderation systems. It works because these algorithms often lack the ability to understand context and nuance. For example, replacing "sex" with "seggs" or "suicide" with "unalive" can bypass filters that are programmed to catch specific words. The primary weakness is that these algorithms are not sophisticated enough to interpret the intended meaning behind these alternative spellings.
What challenges do algorithms face when moderating content in a way that’s fair to users? Are there trade-offs between accuracy and the speed of content moderation?
As an enterprise systems architect working with a variety of big data science algorithms (e.g., linear regression, dimensionality reduction), I oversee algorithms facing several challenges, including understanding context and intent, cultural differences, and evolving language. There is often a trade-off between accuracy and speed. For instance, faster moderation may lead to more false positives or negatives, while more accurate moderation can be slower and resource intensive.
How effective is current AI at understanding context or intent behind words or images? For example, how do algorithms differentiate between harmful content and satire?
Current AI is still limited in its ability to understand context or intent. While it can recognize patterns and specific words, it struggles with nuances like satire, irony, or cultural references. This limitation can lead to both over-moderation (removing harmless content) and under-moderation (failing to catch harmful content).
What risks are associated with over-reliance on AI for censorship? How might this impact freedom of expression or create biases in what users see?
Over-reliance on AI for censorship can lead to inconsistent enforcement, censorship of legitimate content, and lack of transparency. It can also result in shadow banning, where content is subtly suppressed without the user's knowledge. Additionally, AI systems can be biased, reflecting the biases present in the training data. According to Patel, N. (2023), it is important for content creators to be cognizant and current on a platform’s specific guidelines and policies to avoid being shadow banned.
What improvements do you think could be made to content moderation algorithms? Could AI become more sensitive to cultural or contextual nuances in content?
Improvements could include better understanding of context, more transparent processes, and regular updates to keep up with evolving language. Incorporating user feedback and multilingual support can also enhance the effectiveness of these algorithms. Developing more sophisticated natural language processing (NLP) models that understand context and intent can reduce false positives and negatives. Generative AI can help in better understanding the context of content by generating potential interpretations of ambiguous posts. This can assist in distinguishing between harmful content and benign or satirical posts.
How do platforms balance user safety with freedom of expression when designing censorship algorithms? In your opinion, what ethical considerations should guide this balance?
Platforms aim to balance user safety and freedom of expression by setting clear community guidelines, using a combination of AI and human moderation, and providing users with the ability to appeal decisions. They also engage in continuous monitoring and updating of their algorithms to address emerging issues and ensure fairness.
What trends or advancements in AI might impact the future of algospeak and censorship? Is it likely that detection algorithms will adapt to the evolving nature of user-created algospeak?
Advancements in natural language processing (NLP) and contextual understanding could make it harder for algospeak to bypass censorship algorithms. Improved AI models that can better interpret nuances and cultural contexts may reduce the need for coded language. However, as AI becomes more sophisticated, so will the methods used to evade it.
Bibliography
Patel, N. (2023). What Is Shadow Banning? Retrieved from https://neilpatel.com/blog/shadow-banning/: https://neilpatel.com/blog/shadow-banning/
TikTok. (2023). Setting clear rules for the TikTok community. Retrieved from tiktok.com/transparency: https://www.tiktok.com/transparency/en/content-moderation/?form=MG0AV3
Research Gathering for Concurrent and Eventing Web Application Case Studies
James V. Tarlton
11/4/2017
Abstract
Web application development commonly relies on technology stacks such as LAMP (Linux, Apache, MySQL/MariaDB, PHP) and MEAN (MongoDB, ExpressJS, Angular, NodeJS), each offering distinct architectures and databases. While MEAN’s event-driven, non-blocking architecture generally excels at handling high concurrency and real-time applications, LAMP’s mature multithreaded model and relational database remain strong for traditional, data-intensive tasks; studies have yielded mixed results on which architecture is more efficient under different workloads, with each stack showing advantages depending on traffic levels and data sizes. These findings highlight the need for further comparison, including evaluating developer experience using approaches like personal extreme programming (PXP), which adapts agile methods to enhance individual productivity and project outcomes.
Introduction
Developing web applications involves the use of stacks: collections of platforms, frameworks, and libraries. Various researchers have investigated the ability of two popular stacks, LAMP (Linux, Apache, MariaDB, and PHP) and MEAN (MongoDB, ExpressJS, Angular2, and NodeJS) to support web development. Tests of the architectures' relative abilities to support high-performance, high-concurrency web applications have yielded contradictory results, raising questions as to whether performance tests characterized the architectures proper - LAMP's being threaded, MEAN's being event-based - or implementations thereof.
LAMP’s multithreaded archetecture was shown to be less efficent than MEAN’s event-based archetecture. With tests processesing 100 conncurrent tasks, both stacks were fairly similar with Apache's average median being 1.25ms slower. However, with tests processing 1000 concurrent tasks, the difference was significant, equating to Apache being 470ms slower. This showed that an event-based architecture was more efficient than a multi-threaded architecture. However, a different set of similar tests, involving the Knot Pth multi-threaded and Haboob SEDA event-based web servers showed multithreading as more effecient.
Other studies showed LAMP’s relational database to be more efficient for selecting moderately-sized data, especially for aggregation queries, while MEAN’s columnar database was more efficient for selecting big-data (>= 24 terabytes). Craigslist has shown that it is beneficial to use a hybrid database approach, using a relational models for live listings (i.e. for ACID compliance) and using columnar models for historical data (i.e. for memory conservation).
These studies' results suggest the potential usefulness of further, comparative studies of LAMP and MEAN stacks. One direction for such a study, involving the degree to which these architectures facilitate application development, could be addressed using personal extreme programming (PXP), a methodology efficient for personal project management. A PXP development approach leverages learning for individual developers interested in practicing agile methods and personal improvement.
Background
Research was conducted in preparation for a case study of two web stacks – LAMP (Linux, Apache, MariaDB, and PHP) and MEAN (MongoDB, ExpressJS, Angular 2, and NodeJS). This preparation began with a comparison of the stacks’ models, including their architectural and database management models. It continued with a review of research on the usability of the stacks' developmental processes, and concluded with an investigation of project management methodologies for the study.
A web stack architectural model defines a stack’s approaches for handling server-side HTTP requests and persisting data. The LAMP stack supports concurrency with a multithreaded Apache web server. MEAN’s NodeJS web server uses a single threaded event-loop to handle server-side JavaScript concurrency. The research summarized here compared the approaches' performance under low and high loads. The research related to data persistence contrasted MariaDB’s structured, relational data model with MongoDB’s unstructured, columnar model. Simple and complex data manipulation language (DML) operations (e.g. insert, select, aggregated select, etc.) were compared.
Regarding application development, the two stacks differ primarily in the features of the languages they support. PHP (version 7.0.25) exhibits characteristics of traditional programming and scripting languages, while JavaScript (version 1.8.5 / ECMAScript 5) conforms to the tenants of a scripting language. However, noteworthy JavaScript supersets (e.g. Dart, TypeScript, or CoffeeScript) are approaches to overlay object-oriented syntactic sugar like C++ or Java. These languages' relative usability is expected to be a factor in the forthcoming case study, which will involve the development of comparable applications using the two stacks.
Multithreaded and Event-Based Servers
In [1.2], McCune compares the performance of thread-based and event-driven strategies for implementing web servers. These technologies are differentiated at the session layer of the OSI network model. Threaded servers like the Apache framework handle each front-end request with a dedicated thread on the server back-end, implemented in a server-side scripting language such as PHP or Perl. Apache’s approach allows for a simple abstraction of a server's resources: one where each thread is a programmable asset during server-side scripting. By contrast, the more lightweight, event-based approach uses single threaded execution to process requests. For example, the JavaScript-based webserver, Node JS (a.k.a. Node), processes requests using a single event loop that makes concurrent, non-blocking calls to event-specific, asynchronous callbacks. Node's event-loop-based design, together with its stateless libraries and representational-state-transfer- (REST-) based API, account for its high degree of portability.
Authorities have offered contradictory assessments of the technologies' relative merits. In 1979, Lauer and Needham asserted that “[n]either model is inherently preferable, and the main consideration for choosing between them is the nature of the machine architecture.” [1.1] By contrast, in 1999, Dai et al. found that Flash’s event-based webserver exceeded the performance of Apache by up to 50% [1.3]. More recently, Tilkov and Vinoski noted that Node’s single threaded architecture allows for functional programming with easier resource expression and synchronization [1.4]. This contrasts with Apache, which, according to Von Behren et al., is characterized by a "restrictive control flow” that “encourages the programmer to think too linearly about control flow, potentially precluding the use of more efficient control flow patterns” [1.5].
Multithreading, while ideal for various computational tasks, has proven less well suited for web applications. A 2001 study by Welsh et al. [1.7] attributes this to the inability of contemporary platforms to provide sufficient threading “for the tremendous concurrency requirements of an Internet service.” McCune adds that Apache's original design didn't facilitate user-level implementation, leaving synchronization complex and difficult. Implementations of threading, however, have improved over time, including Apache's, and have consistently remained prevalent. The Flash server, by contrast, has become less common with the rise of modern eventing servers such as Node and the Ruby-based EventMachine.
McCune's study sought to determine which approach was better for supporting high-bandwidth, streamed web traffic. McCune compared Apache's performance to that of Node and EventMachine. The reactor-pattern-based EventMachine differs from Node in that its libraries execute on separate CPU threads [1.6]. This makes EventMachine less portable than Node, but also potentially better able to exploit threading. It thus represents a hybrid of multithreading and event-loop programming.
McCune implemented Apache, Node, and EventMachine servers on identical VMWare servers, each with a 3.06 GHz dual core processor and 2 GB of allocated RAM. Snapshots of the VM’s were used to ensure their consistency. Each server framework was subjected to between 1,000 and 1,000,000 synchronous requests and between 100 and 10,000 concurrent requests. Each set of test cases was run twice, first with a single CPU core configuration, then with two cores.
 The three servers exhibited similar maximum response times for 95% of the offered requests. Node's median response times, however, were significantly better than Apache's and EventMachine’s [Figure 1.1]. This suggests event-based systems can consistently handle high levels of synchronous and concurrent requests more efficiently than threaded systems. McCune speculated that EventMachine's use of threaded libraries accounted for Ruby's reduced performance relative to that of Node.
The three servers exhibited similar maximum response times for 95% of the offered requests. Node's median response times, however, were significantly better than Apache's and EventMachine’s [Figure 1.1]. This suggests event-based systems can consistently handle high levels of synchronous and concurrent requests more efficiently than threaded systems. McCune speculated that EventMachine's use of threaded libraries accounted for Ruby's reduced performance relative to that of Node.
The three servers also exhibited similar performance when running on dual-core VMs and subjected to workloads of 1,000 requests, including 100 concurrent requests. Apache, EventMachine, and Node had maximum request times of 29ms, 29ms, and 28ms, respectively. The servers' performances, however, diverged under higher workloads. When presented with workloads of 1,000,000 requests of which 100 were concurrent, Apache’s maximum response time was 862ms, as opposed to 93ms for EventMachine and 73ms for Node. The tests of multicore operation that presented 100 concurrent requests yielded similar results: Apache’s average median was 18.25ms, EventMachine’s was 13.75ms, and Node’s was 17ms [Figure 1.2]. As the level of concurrency was increased to 1,000 concurrent requests, Apache’s performance continued to diminish [Figure 1.3].

 Node also proved to be the most robust of the servers. Apache successfully processed 72.2% of proffered requests, crashing at 991 of 1,000 concurrent requests when running with a single core and 642 of 1,000 when running with two. EventMachine processed 86.1% of its requests under higher levels of
concurrency, crashing at 40,907 of 100,000 requests where 500 were concurrent in single-core operation and at 9,998 of 10,000 in dual-core operation where all 10,000 were concurrent. Node successfully processed 97.2% of its requests, crashing at 351,196 of 1,000,000 requests, 5,000 of which were concurrent. and successfully processing all requests in dual-core operation. That configuration was the only one to successfully complete all of McCune's tests.
Node also proved to be the most robust of the servers. Apache successfully processed 72.2% of proffered requests, crashing at 991 of 1,000 concurrent requests when running with a single core and 642 of 1,000 when running with two. EventMachine processed 86.1% of its requests under higher levels of
concurrency, crashing at 40,907 of 100,000 requests where 500 were concurrent in single-core operation and at 9,998 of 10,000 in dual-core operation where all 10,000 were concurrent. Node successfully processed 97.2% of its requests, crashing at 351,196 of 1,000,000 requests, 5,000 of which were concurrent. and successfully processing all requests in dual-core operation. That configuration was the only one to successfully complete all of McCune's tests.
McCune recommended additional testing, using benchmarking tools for instrumenting the VMs, in order to obtain a clearer picture of the server and kernel resource usage. He suggested further testing with a backend database, which he speculated could yield different results. Finally, his results notwithstanding, McCune commended Apache's feature set and potential power. McCune suggested that Apache might be configured to take better advantage of its platform's threads. While platform support for threading has constantly improved and thread-based designs continue to prevail, McCune agrees that threading may be better suited for computationally-intensive applications.
Multithreaded and Event-Based Servers
In [2.1], von Behren et al. argue that threaded webservers can potentially offer better performance, control flow, synchronization, and state management than event-based webservers. This assessment contrasts with that of Lauer and Needham, who found that event-based and thread-based servers implement equivalent constructs [Figure 2.1] that offer comparable performance [2.3]. Von Behren et al. attributed Lauer and Needham's result to a failure to evaluate thread libraries that were designed "for both high concurrency and blocking operations" [2.6] They speculate that a failure to account for potential performance improvements in thread synchronization skewed Lauer and Needham's results in favor of eventing, which benefitted from synchronization through cooperative task scheduling.
 High overhead amongst the threaded systems and packages HYDRA, Plessey System 250, and Knot [Pth with NesC library] [2.8, 2.9] are attributed to the presence of O(n) length context switch operations throughout one or more threads. These context switches are due to kernel crossings and preemption. They require register save states and kernel crossings, which renders them expensive.
High overhead amongst the threaded systems and packages HYDRA, Plessey System 250, and Knot [Pth with NesC library] [2.8, 2.9] are attributed to the presence of O(n) length context switch operations throughout one or more threads. These context switches are due to kernel crossings and preemption. They require register save states and kernel crossings, which renders them expensive.
Von Behren et al. compared the performance of the event-based SEDA Haboob system to a version of Pth that was optimized by removing context-switch-related operations from the scheduler. This comparison involved the use of a thread pool with up to 100,000 preallocated threads, each of which read an 8kb cached disk file request, to run Welsh et al.'s 2001 [2.2] SEDA benchmark [Figure 2.2]. When running 10 concurrent tasks, Pth and SEDA processed 70,000 requests per second (rps). At 100 concurrent tasks, Pth and SEDA processed 100,000 and 95,000 rps, respectively. Between 100 and 100,000 concurrent tasks, Pth consistently ran 100,000 rps, while SEDA ran between 91,000 and 98,000 rps.
Von Behren et al. also evaluated a second library, Knot, that they designed for high concurrency threading. Knot uses the Coro coroutine library to translate synchronous blocked requests to equivalent asynchronous requests, via UNIX poll() system calls for socket I/O and a thread pool for disk I/O. The authors compared Knot to the Haboob SEDA event-based webserver library [Figure 2.3]. Tests were run on a 2x2000 MHz Xeon SMP with 1 GB of RAM. Knot was tested twice, once favoring active connections over new connections (Knot-C) and once vice versa (Knot-A).
Knot-C’s steady-state bandwidth was measured at approximately 700 Mb/s, as opposed to slightly less than 500 Mb/s for Haboob, which only handles 512 concurrent clients. Von Behren et al. speculated that this limitation was due to the storing of temporary objects in Haboob's single stack. According to the authors, this "affects performance by reducing opportunities for compiler optimizations and by increasing CPU pipeline stalls. [2.1]". Knot avoids these issues with dynamic event handlers, unlike Haboob’s static handlers.
As part of this study, von Behren et al. present three additional arguments on behalf of thread-based architectures. While acknowledging that threads can restrict an application's control flow, the authors note that event-based architectures complicate program design in other, harder to manage ways. Eventing obfuscates control flow and requires users to manually capture a computation's state for analysis and debugging. Additionally, the event-based architecture's use of a single, shared stack creates a need for stack ripping [2.4]: i.e., the reverse engineering of program behavior by decomposing a single stack into a collection of event-specific datasets. This can require analyzing an overwhelming combination of call/return pairs among functions and result in subtle race conditions as well as overly complex testing and debugging. Threading allows programmers to capture live state naturally, where calls and returns are grouped into one-to-one relationships. As the authors note, with threading, “[t]he run-time call stack encapsulates all live state for a task, making existing debugging tools quite effective.” [2.1]
 Threaded servers have been criticized for their use of high-overhead context switching and deadlocks [2.7]. Von Behren et al. reduced the need for these mechanisms through the use of a compiler, nesC, which ensures atomicity between concurrent method calls [2.4]. NesC avoids data races by distinguishing synchronous code only reachable from tasks or from asynchronous code that is only reachable from interrupt handlers. This achieves the same benefits associated with eventing: i.e., the synchronization concurrent logic without the use of mutex/wait-queue mechanisms.
Threaded servers have been criticized for their use of high-overhead context switching and deadlocks [2.7]. Von Behren et al. reduced the need for these mechanisms through the use of a compiler, nesC, which ensures atomicity between concurrent method calls [2.4]. NesC avoids data races by distinguishing synchronous code only reachable from tasks or from asynchronous code that is only reachable from interrupt handlers. This achieves the same benefits associated with eventing: i.e., the synchronization concurrent logic without the use of mutex/wait-queue mechanisms.
Thread stacks have also been criticized as inefficient mechanisms for state management. Von Behren et al. suggest addressing this issue by purging unnecessary state data such as temporary variables before making function calls to execute subroutines. This would involve removing or deindexing all dead variables from all live-state stacks. The authors further suggest the need for compiler support for exception handling for blocked calls.
Based on these findings, von Behren et al. concluded that threaded servers offer can outperform event-based servers, while offering an appropriate model for supporting concurrency. Accordingly, they argue that threading is the more appropriate choice for high-concurrency webserver implementation and abstraction. They picture future work yielding even greater results given tighter compiler integration.
Relational and Columnar Databases
In [3.13], Sattar et al. describe a course that teaches a hybrid approach to managing big data. Big data is defined as including massive, often unstructured [3.5] datasets: i.e., anywhere from 24 terabytes to several petabytes of data in 2012, per Dedić et al. [3.4]. These datasets are being generated in part by increasing numbers of web-based transactions.
Satter et al.'s proposed course approach involves combining a NoSQL database, MongoDB, with a relational database (RDBMS) (Oracle 11g). NoSQL databases are being used extensively in multiple domains [figure 3.1] [3.10], due to their support for fast read transactions, scalability, and tolerance for partitioning [3.7]. MongoDB achieves scalability and partition tolerance by allowing a system's nodes to present different view of a database's state [figure 3.2] [3.6]. Relaxing the RDBMS requirement for view consistency allows transactions to be processed by a subset of a distributed system's nodes [3.9]. It also allows a system's performance to be improved by adding nodes to a distributed system with no changes to the underlying database: a process known as horizontal scaling or sharding.
The need to abandon view consistency to support partitioned operation is in keeping with Brewer's CAP theorem, which holds that data management systems can support only two of three desirable properties for transaction processing systems – i.e. consistency, availability, and partition tolerance [3.6, 3.11]. It also shifts the responsibility for data integrity from the database and business logic from server-side scripts to client-side scripts [3.12].
RDBMSs, according to Parker et al., offer limited scalability, due to their need to ensure that transactions are ACID (atomic, consistent, isolated, and durable). This requirement implies that increases in database capacity require what Sattar et al. refer to as vertical scaling. Vertical scaling entails CPU and RAM upgrades and multi-server data portioning, tedious adjustments to individual queries for schema modifications and normalization routines, and additional logic for assuring atomicity across servers, including adjustments to SQL-based business logic [3.13]. RDBMSs, however, offer better performance for complex aggregation queries [3.7]. They also offer guarantees of semantic integrity that NoSQL databases fail to offer, due to the latter's abandonment of the ACID requirements [3.8].
 E-commerce websites like Amazon's use an RDBMS for the roughly 10% of their data devoted to indexing (e.g., by name or price) and NoSQL for the remaining 90% of their data, including the entities' attributes (e.g. description, color, or size) [3.1]. Similarly, Craigslist migrated their archive site listings to NoSQL while keeping live listings on MySQL [3.3]. Synchronizing their archive to a denormalized data set saves Craigslist substantial memory. Appending the live listings on normalized datasets allows for SQL aggregation.
E-commerce websites like Amazon's use an RDBMS for the roughly 10% of their data devoted to indexing (e.g., by name or price) and NoSQL for the remaining 90% of their data, including the entities' attributes (e.g. description, color, or size) [3.1]. Similarly, Craigslist migrated their archive site listings to NoSQL while keeping live listings on MySQL [3.3]. Synchronizing their archive to a denormalized data set saves Craigslist substantial memory. Appending the live listings on normalized datasets allows for SQL aggregation.
 Sattar et al.'s proposed course devotes the first two thirds of the course to entity-relationship, relational algebra, Oracle-based SQL, and normalization, and the last third to NoSQL (i.e. MongoDB) and frontend code (i.e. JavaScript). Because this is a senior level course, basic programming skills are presumed. The course's final project involves building a hybrid system for a business intelligence application. The proposed system stores dimensional tables (e.g. customer and product records) and fact tables (e.g. sales records) in an RDBMS and large documentation (e.g. product manuals) in a NoSQL database that a frontend dashboard that supports the mapping of key/value pairs to the respective imagery/documentation. This architecture, according to the authors, is typical of ecommerce and self-service websites. [3.2].
Sattar et al.'s proposed course devotes the first two thirds of the course to entity-relationship, relational algebra, Oracle-based SQL, and normalization, and the last third to NoSQL (i.e. MongoDB) and frontend code (i.e. JavaScript). Because this is a senior level course, basic programming skills are presumed. The course's final project involves building a hybrid system for a business intelligence application. The proposed system stores dimensional tables (e.g. customer and product records) and fact tables (e.g. sales records) in an RDBMS and large documentation (e.g. product manuals) in a NoSQL database that a frontend dashboard that supports the mapping of key/value pairs to the respective imagery/documentation. This architecture, according to the authors, is typical of ecommerce and self-service websites. [3.2].
Usability in Scripting Languages
Wang’s 2001 thesis [4.1] used two case studies to assess the usability of Perl 5.6, Active Python 2.0, and Tcl/Tk 8.2. Wang's interest in scripting languages stemmed from their support for rapid development of applications with liberal memory and performance requirements. The style of script development contrasts with systems that are built with programming languages (i.e. C, C++, Java, and Pascal) and that can handle low-level non-functional requirements but require more time to develop.
Three characteristic features of scripting languages are typelessness, interpretation, and expressiveness. Typeless languages allow variables to be used without declarations and to hold values of varying types. Typelessness, as Wang notes, allows for simplified integration of code and data; which makes loosely typed components ideal as reusable interfaces in a variety of contexts. Interpretation allows for dynamic unit testing, avoiding the need for compile-time type inference as required by strictly-typed languages [4.3]. Interpreted code is also text-based, making it portable. Finally, scripting languages tend to be highly expressive [4.3], due to their high level of abstraction [4.4]; this is due to their high extensibility and embeddability, attributable in part to these languages' cross-platform frameworks, libraries, modules, classes, and execution environments [4.1, pages 18-44].
Wang's case studies assessed the effort and challenges associated with developing two applications. One, a front-end intensive application, was a paint program similar to Microsoft’s MS Paint, with support for interactively drawing, moving, and erasing 2D shapes, including lines, rectangles, and ovals. Each instance of this application was implemented with one of its target languages' de facto standard GUI libraries. The other, a back-end intensive application, was a chat program consisting of a TCP chat client and a TCP chat server, the latter of which serviced concurrent TCP client connections; each implemented with the target language's socket library. Using Humphrey's Personal Software Process (PSP) [figure 4.1] as a model for assessing his efforts, Wang tracked how much time he needed to implement each application in each language, how many defects he created, and how much time he needed to fix these defects [4.7]. Wang's taxonomy of defect types focused on defects that could be attributed to language-related issues: i.e., object-orientation (OO) defects, as per the six Chidamber and Kemerer metrics [4.6]; basic construct defects (i.e. data structure, expression, variable, control structure, block delimiter, module import, or scope defects); and library defects or function invocation errors. Defects that were attributable to other issues, including semantic, syntactic, and interface-related defects, were excluded from the study.
 Wang argued that his lack of experience with Python, Perl, and Tcl/TK reduced the risk of biased results. Wang sought to further minimize bias by creating language-independent, detailed designs for the applications before starting development. Additionally, each set of project milestones (i.e. each set of components) was ordered differently to avoid biases stemming from incremental project flow.
Wang argued that his lack of experience with Python, Perl, and Tcl/TK reduced the risk of biased results. Wang sought to further minimize bias by creating language-independent, detailed designs for the applications before starting development. Additionally, each set of project milestones (i.e. each set of components) was ordered differently to avoid biases stemming from incremental project flow.
Total development times for the applications amounted to 1797 minutes for Tcl/TK, 1726 minutes for Perl, and 1201 minutes for Python. Total fix-times (TFTs) for the paint program were 808.4 minutes for the Perl implementation, 684.9 minutes for the Tcl/TK implementation, and 415 minutes for the Python implementation [Figure 4.2]. The Tcl/TK implementation had more defects (144) than the Perl (140), with Python the least (82) [Figure 4.3]. Total fix-times for the chat program were 452.9 minutes for Perl, 232.8 minutes for Tcl/TK, and 162.5 minutes for Python [Figure 4.4]. Defect counts for these programs tracked times, with 67 for Perl, 51 for Tcl/TK, and 45 for Python [Figure 4.5]
For all three languages, library defects accounted for the most time to fix, followed by OO defects and basic constructs. Wang's analysis of. Perl's usability noted the language's limited support for OO, including a lack of a class data type. This, according to Wang, made Perl 5.1 better suited for procedural coding. Objects could not be defined explicitly; inheritance was not supported. Other issues included Perl's poor documentation for its TK (v. 800.022) GUI library; its lack of a non-blocking I/O library, and the socket library's lack of line delimiter management. Wang, however, did cite Perl’s package manager as a useful tool for installing modules from CPAN.



 Wang's analysis of Tcl noted the language's "inconvenient" support for OO logic and array (hash) processing. Perl's [incr Tcl] class is ignored by the garbage collector, which is inconsistent with how Perl handles other classes. One positive was TCL's having the most advanced support for encapsulation via its Private, Protect, and Public data modifiers. Despite the lack of standard support for UDP, standard TCL does support non-blocking I/O and sockets.
Wang's analysis of Tcl noted the language's "inconvenient" support for OO logic and array (hash) processing. Perl's [incr Tcl] class is ignored by the garbage collector, which is inconsistent with how Perl handles other classes. One positive was TCL's having the most advanced support for encapsulation via its Private, Protect, and Public data modifiers. Despite the lack of standard support for UDP, standard TCL does support non-blocking I/O and sockets.
Wang noted Python's apparent lack of support for a platform-agnostic non-blocking I/O library, making Wang’s implementations difficult to port. Despite this, Python was described as the most useful language overall, incurring the fewest number of defects, the least rework time, and the least overall development time. Wang alludes to the Python's standard library “clean and adequate” support of OO programming.
Wang recommended the undertaking of similar studies to assess the usability of other scripting languages such as Ruby and the Microsoft Script Engine, as well as system programming languages such as C++ and Java. Wang regarded PSP as a well-disciplined framework for developing in Perl, TCP, and Python. Additionally, Wang recommended improvements to each of these three languages. For Perl, Wang recommended including better OO support (i.e. a class data type, inheritance, and encapsulation), including Perl/TK GUI in the standard library, supporting socket line delimiter handling, and adding an event loop. For TCL, he recommended making OO and socket libraries standard; also, the inclusion of a package manager and community library for downloading libraries and modules, like Perl’s CPAN. For Python, he recommended the inclusion of an event loop and the addition of a package manager and community library.
Case Study Management
The management of software development projects changed significantly during the late 1990s and early 2000s with the inception of lightweight or agile methodologies, including Extreme Programming (XP) [5.1]. XP was designed for developing high-quality applications in domains with rapidly evolving requirements, where quality is assured through robust communication between the team members and clients. Because XP is based on team building and constant feedback, it cannot be practiced by a singular (individual) developer.
A second methodology, the Personal Software Process (PSP), was developed by Humphry to help individual software professionals to improve as developers. Cockburn attributed interest in PSP to the growth of small tech start-ups [5.2]. PSP asks individuals to track their personal productivity using metrics like lines of code (LOC) written per hour, errors per thousand LOC, and life cycle time ratios. Based on these metrics, activities are planned and estimated, providing means for benchmarking project progress and identifying areas in which developers can improve.
In [5.3], Agarwal and Umphress describe the Personal Extreme Programming (PXP) method, their fusion of the XP and PSP methodologies. PXP attempts to blend XP's agility with PSP's focus on individual improvement through time and defect measurement.
PXP's basic methodology is nearly identical to XP. Like XP, a PXP project's workflow focuses on functional business requirements [Figures 5.1 – 5.4]. In both, development begins with the gathering of requirements, the defining of scenarios, and the development of user stories. These stories are then priced, prioritized based on negotiations with customers, and used to schedule work. Code development is iterative, involving prototyping and test-first programming (i.e. unit and integration testing). Refactoring is also iterative, involving optimizing data models and refining design patterns. Both methods use development, refactoring, and production as baselines to gauge progress.
Agarwal and Umphress adapted XP's twelve core practices for PXP. These practices include planning, incremental releases, metaphors, uncomplicated design, testing, refactoring, pair programming, collective code ownership, continuous integration, adherence to a 40-hour work week, programmer access to an on-site customer, and adherence to coding standards. The authors redefined those XP practices that require two or more people or roles as scaled-down, one-person practices that attempt to achieve the same goals as their XP counterparts. This is accomplished with “role changing”, where a lone developer assumes the various task-related roles prescribed by XP.
 The most complex instance of role changing in PXP involves planning. In XP, planning entails writing user stories (from customers), estimating effort (by programmers), prioritizing stories (by customers), and tracking progress on user stories (by project managers). In PXP, individuals carry out an XP-like planning process by alternating between customer and developer roles.
The most complex instance of role changing in PXP involves planning. In XP, planning entails writing user stories (from customers), estimating effort (by programmers), prioritizing stories (by customers), and tracking progress on user stories (by project managers). In PXP, individuals carry out an XP-like planning process by alternating between customer and developer roles.
Pair programming is a second XP practice that changes under PXP. XP's developer, Beck, argued that pair programming and collective code ownership were essential contributors to code quality, due to the insights obtained through what is essentially an ongoing process of code review. PXP, by contrast, can only require the individual to routinely walk through code between iterations and independently troubleshoot code defects.
Most remaining XP practices carry over unchanged to PXP. In some cases, requiring these practices of individuals rather than teams makes them easier to implement and provides more benefits to the individual. Agarwal and Umphress argue that reducing a development team to a single individual can aid in development by eliminating conflicting interpretations of user stories and designs, disagreements between coders and testers, conflicts over coding standards, and conflicting changes to a code base.
Agarwal and Umphress conclude that PXP balances PSP's higher overhead (i.e. estimations, priorities, tracking) with XPs reduced bureaucracy, blending PSP's focus on rigor with XP's emphasis on feedback, courage, and simplicity. PXP's primary area for improvement would be the need to address its lack of a multi-developer perspective and troubleshooting.
Conclusion
The research reviewed in this document cited clear advantages and disadvantages for the LAMP and MEAN stacks regarding their respective architectural and database models. Other potential bases for comparisons that have not been researched include the stacks' platforms and frameworks. Regarding platforms, a comparison of LAMP and Linux performance and usability with MEAN and its de facto platform, Google’s V8 JavaScript web server may uncover more systematic distinctions between the stacks. A model view controller (MVC) comparison of PHP’s de facto Laravel framework with JavaScript’s Angular framework may provide more developmental distinctions. Finally, scaling the project development team from one person to two or more persons for the same or similar case study may disclose more distinctions between personal development and traditional agile methodologies.
Bibliography
1.1.) Lauer, H.C., Needham, R.M. On the Duality of Operating Systems Structures, in Proc. Second International Symposium on Operating Systems, IR1A, Oct. 1978, reprinted in Operating Systems Review, 13,2 April 1979, pp. 3-19.
1.2.) McCune, R. R. Node.js Paradigms and Benchmarks. Striegel. Grad. Os. F., 2011.
1.3.) Pai, V. S., Druschel P., and Zwaenepoel, W. Flash: An Efcient and Portable Web Server. In Proceedings of the 1999 Annual Usenix Technical Conference, June 1999.
1.4.) Tilkov, S., Vinoski, S. Node.js: Using JavaScript to Build High Performance Network Programs. Internet Computing, IEEE, 2010
1.5.) Von Behren, R., Condit, J., and Brewer, E. Why Events Are a Bad Idea (for high-concurrency servers), Workshop on Hot Topics in Operating Systems, 2003.
1.6.) Schmidt, D. et al. Pattern-Oriented Software Architecture Volume 2: Patterns for Concurrent and Networked Objects. Volume 2. Wiley, 2000
1.7.) Welsh, M., Culler, D., and Brewer, E. SEDA: An Architecture for Well-Conditioned, Scalable Internet Services, ACM Symposium on Operating Systems Principles, 2001.
2.1.) R. von Behren, J. Condit, and E. A. Brewer. Why Events Are a Bad Idea (for high-concurrency servers). Proceedings of HotOS IX.
2.2.) M. Welsh, D. E. Culler, and E. A. Brewer. SEDA: An architecture for well-conditioned, scalable Internet services. In Symposium on Operating Systems Principles, pages 230–243, 2001.
2.3.) H. C. Lauer and R. M. Needham. On the duality of operating system structures. In Second International Symposium on Operating Systems, IR1A, October 1978.
2.4.) A. Adya, J. Howell, M. Theimer, W. J. Bolosky, and J. R. Douceur. Cooperative task management without manual stack management. In Proceedings of the 2002 Usenix ATC, June 2002.
2.5.) D. Gay, P. Levis, R. von Behren, M. Welsh, E. Brewer, and D. Culler. The nesC language: A holistic approach to networked embedded systems. In ACM SIGPLAN Conference on Programming Language Design and Implementation, 2003.
2.6.) Events Can Make Sense by Krohn, Kohler, and Kaashoek
2.7.) J. K. Ousterhout. Why Threads Are A Bad Idea (for most purposes). Presentation given at the 1996 Usenix Annual Technical Conference, January 1996.
2.8.) W. Wulf, R. Levin, and C. Pierson, "Overview of the Hydra Operating System Development," Proceedings of the Fifth Symposium on Operating Systems Principals, Austin, Texas. November 1975.
2.9.) D. M. England, "Capability concept mechanism and structure in System 250," Proceedings of the International Workshop on Protection in Operating Systems, IRIA, Rocquencourt, France, August 1974.
3.1.) Abadi, D. (2010). "Problems with CAP, and Yahoo’s Little Known NoSQL System," DBMS Musings, Retrieved 14 August 2017.
3.2.) Brewer, E. (2012) "CAP Twelve Years Later: How the 'Rules' Have Changed". Computer, Volume 45, Issue 2, pg. 23–29.; IEEE.
3.3.) Butgereit, L. (2010). “Four NoSQLs in Four Fun Fortnights: Exploring NoSQLs in a Corporate IT Environment”. 2Blue Label Telecoms, Nelson Mandela Metropolitan University
3.4.) Dedić, N.; Stanier, C. (2017). "Towards Differentiating Business Intelligence, Big Data, Data Analytics and Knowledge Discovery". Heidelberg, Springer International Publishing.
3.5.) Everts, S. (2016). "Information Overload". Distillations, Chem Heritage. Retrieved 17 February 2017.
3.6.) Gilbert, S.; Lynch, N. (2002) "Brewer’s Conjecture and the Feasibility of Consistent, Available, Partition-tolerant Web Services". SIGACT News, ACM
3.7.) Gill, M. (2014). “Hybrid Deployments: MongoDB and MySQL3 Examples”. Retrieved 15 August 2017. Mehta, C. (2010). “NoSQL is not SQL and That is a Problem”. Retrieved 15 August 2017.
3.8.) Newton, J.; Mason, R. (2017). “Opening Up Possibilities: Discussing the Expansive Power of APIs”. Retrieved 14 August 2017.
3.9.) Parker, Z. (2011). “Comparing NoSQL MongoDB to an SQL DB”. The University of Alabama Center for Advanced Public Safety Tuscaloosa, AL 35487-0290 (205) 348-6363
3.10.) Perroud, B. (2011). “NoSQL Overview: Implementation Free”. Retrieved 13 August 2017.
3.11.) Rewini, H.; Barr, m. (2015). "Advanced Computer Architecture and Parallel Processing". Page 66. John Wiley & Sons.
3.12.) Sattar, A. (2013). "IncorporatIng NoSQL Into a Database Course". Inroads Volume 4 Number 2, ACM
4.1.) Lingyun Wang. (2001). Qualitative Analysis of the Usability of Three Contemporary Scripting Languages: Perl, Python and TCL. East Tennessee State University. August 2001.
4.2.) John Ousterhout. (1998). Scripting: Higher Level Programming for the 21st Century. March 1998, IEEE Computer.
4.3.) Richard Morin, Vicki Brown. Scripting Languages. Sun Expert Magazine, September 1998.
4.4.) Capers Jones. http://www.spr.com/library/0langtbl.htm. March 1996. Software Productivity Research, Inc.
4.5.) David Gillibrand, Kecheng Liu. Quality Metrics for Object-Oriented Design. JOOP, January 1998.
4.6.) S. R. Chidamber, C.F. Kemerer. A Metrics Suite for Object Oriented Design. IEEE Transactions on Software Volume: 20 Issue: 6. Jun 1994.
4.7.) Watts S. Humphrey. The Personal Software Process. Carnegie Mellon Software Engineering Institute. November 2000.
5.1.) Fowler, M. (2003), “The new methodology”, http://www.martinfowler.com/articles/newMethodology.html
5.2.) Cockburn, A. (2004), “Crystal Clear: A Human-Powered. Methodology for Small Teams (The Agile Software Development Series)”, Addison-Wesley Professional.
5.3.) Agarwal, R., Umphress, D. (2008), “Extreme Programming for a Single Person Team (Auburn University)”, ACM












 James "Jim" Vernon Tarlton is a seasoned professional with over
James "Jim" Vernon Tarlton is a seasoned professional with over